- PP: Information is beautiful, worlds biggest data breaches
- PP: FireEye Cyber Threat Map.
- PP: map of current phishing attacks by Netcraft.
- ACT: Phishiest TLDs by Netcraft.
- ACT: Phishiest countries by Netcraft.
- ACT: Phishiest hosters by Netcraft.
- ACT: Phishiest CAs by Netcraft.
- ACT/HIST: Attrition, list of web defacements.
- ACT: Zone-H archive.
- LIST: NIST CPE produts distribution.
- ACT/HIST: ShadowServer - statistics.
- ACT/AV: ShadowServer - AV.
- ACT/INTEL: Arbor Threat Hub & Digital Attack Map.
- ACT/INTEL: Arbor & Google Digital Attack Map.
- ACT/INTEL: Arbor ATLAS portal.
- ACT/HONEY: HoneyNet Project Map.
- ACT: Ipillion.
- ACT: Zeus, ransomware, ... trackers.
- ACT: Team Cymru graphs.
- ACT: Team Cymru, Malicious Activity Movies.
- ACT: Team Cymru, Malicious Activity Maps.
- ACT/LEGACY: Attrition.org, website defacements.
- ACT/LEGACY: Alldas.de, website defacements.
- ACT: Zone-H, website defacements.
- ACT: Kaspersky CyberThreat Real-Time Map.
- REP: Verizon Data Breach Investigations report, 2018.
- REP: Cisco Security Reports.
- REP: Cisco Security Report: 2017.
- REP: Verizon Data Breach Investigations Report (10th edition).
- REP: Arbor Annual Worldwide Infrastructure Report.
- REP: Arbor Worldwide Infrastrure report Volume XI.
- REP: IBM X-FORCE Threat Intelligence Index.
- BLOG: BeyondTrust Blog.
- BLOG: Snort IDS blog.
- BLOG: Cisco/TALOS Intel blog.
- BLOG: CORE Security.
- BLOG: G-Laurent.
- BLOG: Krebs on Security.
- NEWS: Ars Technica on security.
- BLOG: Symantec Security Response.
- BLOG: Symantec Security Center.
- BLOG: Cisco blogs.
- BLOG: Darknet UK.
- BLOG: MalwareBytes Labs.
- BLOG: DEF Intel blog.
- NEWS: US CERT GOV.
- NEWS: US CERT GOV, ALERTS.
- BLOG: Cisco OpenDNS/Umbrella.
- BLOG: Threatpost by Kaspersky.
- BLOG: Kaspersky Lab Daily.
- BLOG: Rapid7 Community.
- BLOG: Social Engineer.org.
- NEWS: The Register UK on security.
- NEWS: Slashdot.
- NEWS: State of Security, Tripwire.
- BLOG: Lcamtuf.
- BLOG: Troy Hunt.
- BLOG: Errata Security.
- BLOG: PortSwigger / BurpSuite.
- BLOG: Google Project Zero Team.
- BLOG: SecurityFocus.
- BLOG: Trend Micro.
- NEWS: Security Focus.
- BLOG: Unit42 Threat Research (Palo Alto).
- NEWS: Palo Alto research center.
- NEWS: Dark Reading.
- NEWS: NeoHapsis Blog.
- NEWS: Hexacorn Blog.
- NEWS: Pentest Monkey.
- BLOG: JPCert CC Official Blog.
- NEWS: IBM X-Force Exchange.
- BLOG: Objective-See (Mac OSX Focus).
- BLOG: news from the F-secure lab.
- CORPNEWS: Bitdefender Business Insights.
- BLOG: MalwareTech.
- BLOG: Metasploit community blog.
- BLOG: Metasploit Rapid7 blog.
- BLOG: Naked Security by Sophos.
- BLOG: Trustwave SpiderLabs.
- BLOG: OWASP (web).
- BLOG: FireEye Threat Research Blog.
- BLOG: FOX IT.
- NEWS: Wired, security.
- BLOG: lcamtuf.
- NEWS: CERT, Carnegie Mellon University.
- BLOG: GOATSE FR.
- NEWS: CERT-EU, Computer Emergency Response Team for EU institutions.
- BLOG: ShadowServer.
- BLOG: Arbor Networks.
- NEWS: Arbor resources - NETSCOUT.
- NEWS: Honeynet Project.
- BLOG: Swiss Security Blog.
- BLOG: Dragon News by Team Cymru.
- BLOG: Schneier on Security.
- BLOG: TrendsLab - Security Intelligence.
- BLOG: SANS ISC INFOSEC - INTERNET STORM CENTER.
- BLOG: Bunnie's blog.
- BLOG: SipVicious (VOIP).
- BLOG: Virus Bulletin.
- NEWS: Reuters #cyberrisk.
- BLOG: Akamai Threat Advisories.
- BLOG: Akamai Security Blog.
- BLOG: Radware, DDoS Chronicles.
- BLOG: Microsoft Windows Server blog.
- HISTORY: attrition.org.
- BLOG: BeEF Project.
- BLOG: Maltego.
- NEWS: Bleeping Computer.
- NEWS: Computer Securty Division, Computer Security Resource Center (NIST).
- NEWS: TechBeacon, Security.
- NEWS: MIT Technology Review.
- NEWS: weekly vulnerability bulletins by US CERT.
- BLOG: a few thoughts on cryptographic engineering.
- BLOG: Google Security Blog.
- NEWS: ZDNet, Security.
- BLOG: Sucuri.
- BLOG: Qualys.
- NEWS: HelpNetSecurity.
- BLOG: AlienVault blogs.
- SITE: HD Moore.
- BLOG: GoPhish.
- NEWS: gbhackers.com.
- NEWS: HackerNoon.
- NEWS: The Hacker News.
- NEWS: Cloudflare Blog.
- NEWS: MIT Tech Review.
- BLOG: EvilSocket.
- BLOG: RM-IT.de.
- BLOG: Bitdefender Labs.
- BLOG: Microsoft Security TechCenter.
- BLOG: Symantec Security Blog.
- BLOG: pentestit.com.
- BLOG: Pen Test Partners Blog.
- BLOG: Tenable (Nessus) Blog.
- BLOG: Hack Read.
- NEWS: SANS ISC Diary.
- BLOG: Check Point Security.
- BLOG: OpenBSD Journal.
- BLOG: ZDNet Zero Day.
- BLOG: ASERT by Arbornetworks.
- BLOG: Cloudflare.
- BLOG: we live security (ESET).
- BLOG: Omar Santos (Cisco Security).
- NEWS: SC Media.
- BLOG: Chris Sanders.
- NEWS: Dark Reading.
- MAIL: Nmap Announcements.
- MAIL: Full Disclosure.
- MAIL: BUGTRAQ.
- MAIL: Penetration Testing.
- MAIL: Info Security News.
- MAIL: Firewall Wizards.
- MAIL: IDS Focus.
- MAIL: Web App Sec.
- MAIL: Daily Dave.
- MAIL: HOneypots.
- MAIL: Microsoft Security Notifications.
- MAIL: US CERT Advisories.
- MAIL: Open Source Security.
- MAIL: Metasploit.
- MAIL: SNORT.
- MAIL: SiGMil-1.
- ENUM: Netcraft site report.
- ENUM: ICANN WHOIS.
- ENUM: RIPE.
- ENUM: RIPE Query Tools.
- ENUM/GOOGLE: Exploit DB Google Hacking DB.
- ENUM/GOOGLE: Google Hacking DB, hackers for charity.
- ENUM: Shodan IO database.
- ENUM: Internet-Wide Scan Data Repository.
- ENUM: research data on Internet-wide scanning.
- ENUM: Nmap Network Scanner.
- ENUM: Angry IP Scanner.
- ENUM/DOC: Angry IP scanner, documentation.
- ENUM: MS DEV, IcmpSendEcho function.
- ENUM: Solarwinds Engineers Toolset.
- ENUM: Colasoft Ping Tool.
- ENUM: Hping, command-line TCP/IP assembler/analyzer.
- ENUM: Hping (github).
- ENUM: Hping3.
- ENUM: Hping Wiki.
- ENUM/PROT: Wikipedia, Transmission Control Protocol (TCP).
- ENUM/PROT: Wikipedia, User Datagram Protocol (UDP).
- ENUM/PROT: Wikipedia, Internet Control Message Protocol (ICMP).
- ENUM/PROT: IBM knowledge center, comparison of IPv4 and IPv6.
- INFO: market share statistics for Internet Technologies.
- ENUM/TOOL: The ZMap Project, home of ZMap, ZGrab, ZDNS, ...
- PAPER: ZMap: fast Internet-Wide scanning and its security applications.
- ENUM: Usersearch.org: find the person behind a username, email address or phone number.
- ENUM: reverse DNS WHOIS and more.
- ENUM: the opensource intelligence resource disovery toolkit.
- ENUM: 101+ OSINT resources for investigators.
- PUB: CIA, sailing the sea of OSINT in the information age.
- ENUM: Wikipedia on Intellipedia.
- ENUM: EFF, DocuColor Tracking Dot Decoding Guide.
- ENUM: EFF, list of printers which do or no not display tracking dots.
- ENUM: The Internet Archive - Wayback Machine.
- ENUM/SURVEY: DNS, the measurement factory.
- ENUM: recon-ng (OSINT).
- ENUM: Maltego.
- ENUM: IVRE, network recon framework.
- ENUM: OSINT dbase CN.
- ENUM: Google Hacking Database.
- ENUM: Google hacking database - HFC.
- ENUM: Dogpile, multiple search engines at the same time.
- ENUM: the info, multipe site search.
- ENUM: PolyCola, dual site search, compare results.
- TOOL/ENUM: SearchDiggity.
- ENUM: ARIN.
- ENUM: APNIC.
- ENUM: RIPE.
- ENUM: RIPE, queries and faq.
- ENUM: LACNIC.
- ENUM: AFRINIC.
- ENUM: flumps.org (historical).
- ENUM: ICANN WHOIS.
- ENUM: OSINT, The Harvester.
- IDS/IDP: Security Onion.
- IDS/IDP: Snort IDS.
- IDS/IDP: Snort IDS blog.
- IDS/IDP: Test my IDS page.
- IDS/SIG: Juniper Network signatures.
- IDS/MON: Ntop-ng: packet capture, traffic recording, network probe, analysis.
- MON/SNIFF: NDPI, L7 deep packet inspection library.
- MON/SNIFF/FLOW: IVRE, network recon framework.
- SNIFF: TCPDump.
- SNIFF: Wireshark.
- SNIFF: Agilent Advisor LAN.
- SNIFF: Colasoft Capsa free network analyzer.
- SNIFF: Windump, TCPDump for Windows.
- SNIFF: Colasoft Packet Builder.
- SNIFF: Colasoft Packet Player.
- SNIFF: EtherApe: a graphical network monitor.
- SNIFF: driftnet, inspired by EtherPEG.
- SNIFF: driftnet (github).
- SNIFF: EtherPEG: MAC (driftnet-like).
- SNIFF/PHY: USB snooping made easy: crosstalk attacks on USB hubs.
- SNIFF: TraceWrangler, easy sanitization and anonymization of PCAP(ng) files.
- VULN: Android Source - Security.
- VULN/HISTORY: Security Administrator Tool for Analyzing Networks (SATAN).
- VULN/SCAN: Beyondtrust Retina.
- VULN/LIST: CVE Details.
- VULN/LIST: CORE updates and modules.
- VULN/EXPL: Packetstorm Security.
- VULN/NEWS: Secunia Research, vulnerabilities discovered.
- VULN/NEWS: Cisco Security on Vulnerabilities (Cisco/non-Cisco).
- VULN: Akamai Information Security Research.
- VULN/EXPL: Dirty Cow (CVE-2016-5195).
- VULN/INFO: Dirty Cow RHEL BUG 1384344.
- VULN/EXPL: Dirty Cow details.
- VULN/EXPL: Dirty Cow PoCs.
- VULN/EXPL: Wikipedia on Dirty Cow.
- VULN/EXPL: LIveOverflow with an excellent explanation vidoe on Dirty Cow.
- VULN/EXPL: Exploit DB.
- VULN/EXPL: Vulnerability Lab.
- VULN/EXPL: Rapid7/Metasploit Exploit DB.
- VULN/SCAN: OpenVAS.
- VULN/SCAN: OpenVAS VM.
- VULN/LIST: CERT.org, vulnerability notes database.
- VULN/LIST: US NIST, National Vulnerability Database.
- VULN/LIST: Search NVD.
- VULN/LIST: SecuriTeam.
- VULN/SYS: CVSS, Common Vulnerability Scoring System.
- VULN/LIST: Common Weakness Enumeration (CWE), community-developed list of software weakness types.
- VULN/LIST: CVE DETAILS.
- VULN/EXPL: Heartbleed (CVE-2014-0160).
- VULN/SCAN: Heartbleed test by filippo.io.
- VULN/INFO: ShellShock (Bash) CVE-2014-6271.
- VULN/INFO: Troy Hunt, "Everything you need to know about the Shellshock Bash bug".
- VULN/INFO: Symantec, "All you need to know about the bash bug vulnerability.
- VULN/POC: Linux kernel 2.6.32 < 3.x.x PERF_EVENTS privilege escalation.
- VULN/POC: CVE-2017-7240, Miele Professional PG 8528 PST10 directory traversal attack.
- VULN/POC: CVE-2017-7240, Miele Professional PG8528.
- VULN/PATCH: MS17-010: MS SMB Server (4013389).
- VULN: Sybase directory traversal.
- VULN: Complete FTP server.
- VULN: Snugserver FTP server.
- TOOL: dotdotpwn, directory vulnerability fuzzer.
- TOOL: dotdotpwn, home.
- VULN: OWASP on path traversal/directory traversal.
- VULN: Wikipedia on OWASP.
- VULN: VSFTPD compromised source packages backdoor vulnerability.
- VULN: Alert: vsftpd download backdoored.
- VULN: Juniper/ScreenOS backdoor, CVE-2015-7755, CVE-2015-7756.
- VULN: CVE-2015-7755.
- VULN: MS10-015 - User mode to ring esclation (KiTrap0D).
- VULN: Linux Kernel 2.6.32 < 3.x.x PERF_EVENTS privilege escalation.
- VULN: Wikipedia on ETERNALBLUE.
- VULN: CVE-2017-0144 used by ETERNALBLUE, SMBv1 vulnerability.
- VULN: Microsoft Technet Security Advisories.
- VULN: Microsoft Security Updates.
- VULN: Wikipedia on race condition errors.
- VULN: Rapid7 on MacOSX SUDO/TIME vulnerability (CVE-2013-1775).
- VULN: SUDO MacOSX SUDO/TIME vulnerability (CVE-2013-1775).
- VULN: MS02-045, SMBDIE.
- VULN/PAPER: SMBdie'em All - Kill that Server, Kirby. SANS.
- MEM: "7. Memory: Stack vs Heap, Paul Gribble.
- VULN: MS16-137-LSASS DoS (G-Laurent).
- VULN: SMB Tree DoS, VU 867968.
- VULN: CVE-2017-016.
- VULN/POC: CVE-2017-016 (Laurent Gaffié).
- VULN: F-Secure, find out more.
- VULN: SMBLoris.
- VULN: Rapid7 Community, SMBLoris - what you need to know.
- VULN: packetstorm, SMBLoris PoC.
- VULN: directory traversal attack.
- VULN: Security Focus, escaped character decoding vulnerability.
- VULN: Security Focus, extended unicode vulnerability.
- VULN: CVE Details on MS directory traversal vulnerabilities.
- VULN: Bypassing UAC with User Privilege under Windows Vista/7 - mirror, Muts.
- VULN: CVE-2010-4398, stack based overflow in win32k.sys.
- VULN: NVD - CVE-2010-4398.
- ENUM: IVRE, network recon framework.
- VULN: weekly vulnerability bulletins by US CERT.
- VULN: CVE DETAILS.
- VULN: SecuriTeam.
- TOOL: nmblookup (SAMBA), NetBIOS over TCP/IP client to lookup NetBIOS names.
- TOOL: smbclient (SAMBA), ftp-like client to access SMB/CIFS resources on servers.
- TOOL: enum4linux, wrapper around the tools in SAMBA for easy fingerprinting.
- VULN: MS10-061, vulnerability in Print Spooler Service could allow remote code execution (23472909).
- TOOL: Rapid7 on MS10-061
- VULN: MS10-061, printer spooler vulnerability.
- TOOL: AWS S3 scanner.
- TOOL: AWS S3 Bucketeers.
- TOOL: AWS Bucket Dump.
- TOOL: AWS Bucket enumeration through certificate transparancy lists.
- TOOL: Slurp, enumerate S3 buckets manually or via certstream.
- TOOL: Bucket Stream, enumerate S3 buckets via certstream.
- VULN: CVE-2016-4484: CryptSetup Initrd Root Shell.
- VULN: CVE-2018-1111, DHCP client script code execution vulnerability.
- TOOL: TrickURI (Google), verify if browsers display an URL correctly.
- IND: US, Industrial Control Systems Cyber Emergency Response Team.
- Fuzzing and related:
- FUZZ: Wikipedia on Fuzzing.
- FUZZ: 01.org, Intel Open Source, Linux Kernel performance and 0day testing.
- FUZZ: Microsoft White Box Fuzzer - Security Risk Detection.
- FUZZ: Microsoft, automated penetration testing with white-box fuzzing.
- FUZZ: Google OSS-FUZZ.
- Web & App related:
- WEB: Wep App Sec.
- WEB: OWASP.
- WEB: OWASP Testing Project.
- WEB: OWASP Web Goat, vulnerability learning environment.
- WEB: OWASP Broken Web Applications.
- WEB: OWASP Web Goat (Github).
- APP: OWASP iOS application vulnerability learning.
- WEB: dotdot pwn examples (directory traversal fuzzer).
- WEB: OWASP Zed Attack Proxy.
- WEB: OWSP TOP TEN Project.
- WEB: UNICODE.
- WEB: escaped characters.
- WEB: HTML Tag.
- WEB: Blind Elephant, web application scanner (SF).
- WEB: Blind Elephant, web application scanner (Qualys).
- WEB: Whisker (Rain Forest Puppy, RFP).
- Databases and co:
- SQL: Wikipedia on Structured Query Language.
- NoSQL: Wikipedia on NoSQL.
- DB/SQL: Oracle on DB & SQL concepts.
- SQL: W3Schools, introduction to SQL.
- SQL: KHAN Academy: Intro to SQL: Quering and managing data.
- Pluralsight: free online course, introduction to SQL.
- SQL: SQLBolt, learn SQL with simple, interactive exercises.
- SQLi: Wikipedia on SQLinjection.
- Social:
- SE: users really do plug in USB drivers they find, University of Illinois.
- SE: CompTIA, find a flash drive, pick it up.
- SE: GoPhish, open source (demo) phishing tool.
- SE: Wikipedia on Punycode.
- SE: IDN in Chrome.
- SE/TOOL: Mailinator: millions of public, disposable email inboxes.
- SE/TOOL: Free SMS verification, receive SMS online.
- SE/TOOL: BurnerAPP - calling, texting, picture messaging.
- SE/TOOL: TempoPhone - temporary phone number.
- SE/TOOL: 10 minute mail.
- SE/TOOL: Guerrilamail.com.
- SE/TOOL: DisPostAble.
- SE/TOOL: Hushed, disposable numbers.
- SE/TOOL: King Phisher.
- SE/SPF: DMARC Analyzer: What is SPF?
- SE/SPF: DMARC Analyzer: SPF Record Check.
- SE/TOOL: Duck Toolkit.
- SE: USB IDs.
- SE/TOOL: Rubber Ducky Manual.
- SE: Bash Bunny by Hak5.
- SE: Bash Bunny Manual.
- SE: Bash Bunny: Quick Creds.
- SE/TOOL: Rubber Ducky Scripting Language.
- SE/TOOL: Rubber Ducky: obfuscation and optimalization.
- SE: Security Awareness with USB Rubber Ducky.
- SE: hak5darren, Rubber Ducky home and code.
- SE: PortaPow - Data Blocker.
- SE: Mitnick, LinkedIn 2 factor authentication.
- SE: USBNinja, a BadUSB remake.
- SE: Sneak Technology.
- SE: Lab401 gear.
- SE: Wikipedia on Juice Jacking.
- SE: _MG_ BadUSB Cable: https://twitter.com/_MG_/status/949684949614907395.
- SE: Wall of Sheep.
- Research, researchers, PoCs:
- RES/POC: Laurent Gaffie.
- RES/POC: Rain Forest Puppy (RFP).
- RES/POC: Didier Stevens (Labs).
- RES/POC: Tavis Ormandy (Google).
- VULN/POC: MS-10-015 Kitrap0d.
- VULN/PAPER: Papers, Exploit Database.
- RES/POC: Exploit Database.
- RES/POC: ShellShocker - ShellShock.
- SCAN: Nmap Network scanner.
- RES/POC: Chris Gates, Carnal0wnage.
- RES/POC: SubTee.
- RES/POC: Sow Ching Shiong.
- RES/BLOG: Chris Evans - ScaryBeasts.
- RES/POC: Michal Zalewski, lcamtuf.coredump.cx.
- RES/POC: Niels Provos.
- RES/POC: packetstorm on RFP (Rain Forest Puppy) tools (whisker, ...).
- RES/POC: Frizk.
- Phreaks:
- Wifi, bluetooth, ... :
- WIFI: Aireplay-ng / Aircrack-ng.
- Bluetooth: Armis - BlueBorne attack.
- RADIO: Wikipedia on Software Defined Radio.
- WIFI: KRACK (project page), Key Reinstallation Attacks (KUL).
- WIFI: Tweakers, (dutch) Krack aanval op WPA2.
- WIFI: KRACK, key re-installation attack demo (KUL) (Youtube).
- Organizations and related:
- ORG: Forum for Incident Response and Security Teams (FIRST).
- ORG: Belgium, Federal Cyber Emergency Team (CERT.be).
- ORG: Belgium, Centre for Cyber Security Belgium (CCB.be).
- ORG: Interpol on Cybercrime.
- ORG: Belgian, Federal Police, Computer Crime Unit (FCCU).
- Credentials:
- PROT: Wikipedia on LLMNR.
- PROT: IETF on LLMNR.
- PROT: MS Cableguy on LLMNR.
- PROT: Wikipedia on WINS.
- TOOL: Responder, LLMNR, NBT-NT, MDNS poisoner.
- PROT: Wikipedia on MDNS, Multicast DNS.
- PROT: Wikipedia on NTLMSSP.
- PROT: MS on NTLMSSP.
- PROT: Wikipedia on WPAD, Web Proxy Auto-Discovery Protocol.
- PROT: WikiPedia on LM Hashing.
- PROT: http: WikiPedia on Code Page 1252.
- PROT: WikiPedia on MD4.
- PROT: Microsoft on LSA.
- PROT/TOOL: calculate LM and NTLM hashes.
- PROT/TOOL: calculate LM and NTLM hashes.
- PROT/TOOL: l0phtcrack.
- PROT: Wikipedia on MS SYSKEY.
- PROT/CONF: enabled MS SYSKEY.
- PROT: Wikipedia on SMB.
- TOOL: John The Ripper Cheat Sheet (pentestmonkey).
- PROT: Technet Magazine on NTML.
- PROT: Xfocus on NTLM/SMBRelay attack.
- Other, related tools:
- TOOL: Evilgrade Framework.
- TOOL: Hidden-Tear, open source ransomware honeypot.
- TOOL: Social Engineer Toolkit.
- TOOL: Fing App, free network scanner for IOS/Android.
- MALWARE DEMO: Hidden Tear.
- TOOL: Portswigger Web Security, Burp Suite Editions.
- TOOL: Hopper, MacOS and Linux disassembler.
- TOOL: Aircrack-ng, Airbase-ng.
- TOOL: Metasploit, penetration testing toolkit by Rapid7.
- TOOL/INFO: Metasploit MSF-RPC.
- TOOL: Charles, web application proxy.
- TOOL: MITM Proxy.
- TOOL: Fiddler, free web debugging proxy.
- TOOL: The Backdoor Factory (BDF), patching files with shellcode.
- TOOL/INFO: DerbyCon 2013, Midnite Runr: Patching windows executables with the backdoor factory.
- TOOL/NSA: Quantum Insert emulation tool by Fox-it.
- TOOL/TCP: Shijack.
- TOOL/TCP: HUNT.
- TOOL/MITM: Ettercap.
- TOOL/INFO: The Harvester.
- TOOL/INFO: The Harvester (github).
- TOOL/REPLAY: Firesheep by Codebutler.
- TOOL/REPLAY: Firesheep (github).
- TOOL/MITM: PuttyRider.
- TOOL/CRED: Meterpreter Incognito, impersonate Windows user tokens on a compromised machine.
- TOOL/CRED: Crunch - wordlist generator.
- TOOL: original home of Netcat.
- TOOL: original home of fscan.
- TOOL: BeEF, the Browser Exploitation Framework project.
- TOOL/WIKI: BeEF, wiki.
- TOOL: (List) SecTools.org.
- TOOL: Core Impact, solution for testing and assessing vulnerabilities.
- TOOL: Core Impact, open source tools.
- TOOL: SSH-MITM (proxy, github).
- TOOL: Recon-NG - OSINT gathering tool.
- TOOL: OllyDBG 32-bit assembler level debugger for Windows.
- TOOL: SecLists - various security related lists.
- TOOL: SSLStripv2.
- TOOL: Delorean, NTP spoofer. µ
- TOOL: Eleven Path, home of The FOCA and other tools.
- TOOL: MWR Labs, Android, Ios, ...
- TOOL: Backbox Linux, penetration testing distribution.
- Denial of Service (DoS):
- DOS: MS16-137 LSASS.
- DOS: VU#867968, MS SMB Tree Connect Response DoS.
- DOS: VU#867968 SMB Tree PoC.
- DOS: Wikipedia on (D)DoS.
- DOS: Wikipedia on radio jamming.
- DOS: How stuff works, Ebomb (EMP).
- DOS: Wikipedia on EMP weapons.
- DOS: The growing threat from an EMP attack.
- DOS: US, Space Weather Prediction Center.
- DOS: BOEING CHAMP.
- DOS: National Post: how Boeings non-lethal CHAMP missiles could mark a new ara in modern day warfare.
- DOS: CTVNEWS, most powerful solar flare in a decade triggers storm warning.
- Distributed Denial of Service:
- DDOS: Wikipedia, 2007 cyberattacks on Estonia.
- DDOS: Wikipedia, 2010 cyberattacks on Myanmar.
- DDOS: Wikipedia, US diplomatic cables leak.
- DDOS: Wikipedia: Operation Payback.
- DDOS: Arbor, understanding DDoS.
- DDOS: Wikipedia, 2012, Operation Ababil.
- DDOS: Radware - Operation Ababil.
- DDOS: Verisign.
- DDOS: Verisign DDOS 2017.
- DDOS: wikipedia on Mirai.
- DDOS: SMURF amplifier monitor.
- DDOS: BASHLITE.
- DDOS: incapsula, malware analysis Mirai DDoS botnet.
- PROT: Wikipedia on CHARGEN.
- PAPER: Berkeley, an analysis of using reflectors for Distributed Denial of Service attacks.
- DDOS: flawed router flood university of Wisconsin Internet Time Server.
- DDOS: open letter to D-LINK about NTP vandalism.
- DDOS: CVE-2013-5211, NTP MON_GETLIST issues.
- DDOS: Cisco - CVE-2013-5211.
- DDOS: Open Resolver Project (DNS).
- DDOS: Cloudflare, Memcrashed - major amplification attacks from UDP port 11211.
- DDOS: GITHUB, Memcashed protocol.
- DDOS: Nucleus.be, Memcached gebruiken: wie, wat, waar?.
- Physical:
- PHY: CCC breaks iris recognition system of the S8.
- PHY: hacking the Samsung Galaxy S8 Irisscanner.
- BIO: KUL/ESAT, vingerafdrukken op de Belgische EID, technische analyse.
- VoIP:
- VOIP: Wikipedia on SIP.
- VOIP: Asterisk NOW platform.
- VOIP: Wiki Asterisk NOW.
- VOIP: FREEPBX.
- VOIP: X-lite softphone.
- VOIP/TOOL: SIPvicious.
- VOIP/TOOL: SVWar.
- VOIP: Cisco Security SIPvicious signature.
- VOIP/TOOL: Hacking Exposed (book), tool list.
- Tunneling & covert channels
- TUNNEL: TCP trough DNS.
- TUNNEL: Hping3.
- COVERT: Wikipedia on Covert Channel.
- COVERT: Iodine, ipv4 tunnel over DNS.
- COVERT: Iodine, github.
- COVERT: storage/store data in ICMP packets.
- Authentication:
- EAP: Wikipedia on EAP.
- EAP: Cisco on EAP-FAST.
- EAP: Cisco on EAP-FAST configuration with wireless controllers.
- MACsec/VPN: Wikipedia on 802.1AE
- MACsec/VPN: Juniper on 802.1AE
- AUTH: Password Security - a case history by Robbert Morris and Ken Thompson.
- Virtualization:
- VIRT: VMware, determine if VT-X is enabled without rebooting ("esxcfg-info | grep "HV Support").
- VIRT/FW: Check Point vSEC Virtual Edition (VE).
- VIRT/FW: Check Point, Introduction to VSX.
- VIRT/SEC: Trend Micro Deep Security.
- Intelligence:
- INTEL: SPAM, Composite Blocking List.
- INTEL: NVD data feeds.
- SYNT: VERIS, vocabulary for event recording and incident sharing.
- INFO/INTEL: IBM X-Force Exchange.
- INFO/INTEL: Cisco, latest threat information.
- YARA: malware signatures.
- INTEL/YARA: YARA documentation.
- INTEL/MAL: ShadowServer, test executables against known software application list.
- INTEL/GEOIP: Shadowserver, IP/ASN/GEO IP.
- INTEL/MAL: Malware Patrol, Open Source.
- INTEL/MAL: Team Cymru - Malware Hash Registry.
- SIGINT: Wikipedia on Signals Intelligence (SIGINT).
- OSINT: Wikipedia on Open Source Intelligence.
- LOGGING/SIEM: Generic Signature Format for SIEM systems.
- SANDBOX: Hybrid Analysis.
- INTEL/TIP: Eclecticiq open-source software.
- GRAPH: Graphite, stoer and graph metrics.
- MON: Prometheus, open source metrics and alerting.
- Hardening:
- HARD: National Checklist Program Repository.
- HARD: FIRST Best Practice Guide Library (BPGL).
- HARD: CCB.be documents.
- HARD: Common Weakness Enumeration.
- HARD: INTEL NX.
- HARD: Microsoft Enhanced Mitigation Experience Toolkit (EMET).
- HARD: Krebs on EMET.
- HARD: Wikipedia on Security Enhanced Linux.
- HARD: Wikipedia on Linux AppArmor.
- HARD: Microsoft Security Response Center.
- Unsorted, various:
- LEGACY: Eric Steven Raymond, "How to become a hacker".
- LEGACY: Phrack, "The Hackers Manifesto".
- MAGAZINE: PHRACK.
- BLOG: Parisa Tabriz, "So, you want to workin security?".
- LEGACY: TCP session hijacking by Cheese.
- LEGACY: Michal Zalewski, strange attractors and TCP/IP sequence number analysis - one year later.
- LEGACY: CERT.ORG, statistical weaknesses in TCP/IP Initial Sequence Numbers
- https://www.google.be/url?sa=t&rct=j&q=&esrc=s&source=web&cd=1&cad=rja&uact=8&ved=0ahUKEwilye3w-sHUAhWHJVAKHVqlAQgQFggjMAA&url=http%3A%2F%2Fwww.dcs.ed.ac.uk%2Fhome%2Frah%2FResources%2FSecurity%2Fadmin_guide_to_cracking.pdf&usg=AFQjCNGoPM9uAKR1XI416lxphdboRkEfUA&sig2=FFdCB5vJ44hge_6YiXVlAQ">LEGACY: Dan Farmer, Improving Security of Your Site by Breaking into it.
- SEC: NIST, CyberSecurity Framework.
- SEC: Pwnie Awards!
- SEC: Wikipedia on XKeyscore.
- LEAK: Wikipedia on "The Shadow Brokers".
- ACT: Wikipedia on "The Equation Group".
- ACT: Wikipedia on "Tailored Access Operations" (TAO), NSA.
- LEAK: Wikipedia on the NSA ANT catalog.
- ACT: Wikipedia on Government Communications Headquarters (GCHQ).
- INTEL: Wikipedia on ECHELON.
- PHY: Wikipedia on TEMPEST.
- LEAK: Wikipedia on Edward Snowden.
- LEAK: Wikipedia on global surveillance disclosures (2013-present).
- LEAK: Wikipedia on Chelsea Manning.
- LEAK: Wikipedia on Reality Winner.
- LEAK: The Guardian - the NSA files decoded.
- LEAK: Wikipedia on XKeyscore.
- LEAK: Wikipedia on Special Source Operations.
- LEAK: Wikipedia on Special Collection Service.
- Forensics:
- FOR: Wikipedia, list of file signatures.
- FOR: Wikipedia, Windows Portable Executable (PE).
- FOR: Wikipedia, Dynamic Linker.
- FOR: Wikipedia, COF (UNIX).
- FOR: Microsoft, PE file format.
- FOR: MSDN, peering inside the PE file format.
- FOR: Wikipedia, Code Cave.
- FOR: Wikipedia, UPX packer.
- FOR: INFOSEC, demystifying PE file.
- FOR: why spot checking Cisco equipment for counterfeit signs is necessary.
- FOR: The Volatility Foundation.
- FOR: Wikipedia on Volatility.
- FOR: Wikipedia on Apple File System (AFS).
- FOR: SANS DFIR, Digital Forensics and Incident Response.
- FOR: Web browser user agents.
- FOR: HTTP USER AGENT string explained.
- Software Defined Networking (SDN):
- SWITCH: Cisco Switching Fundamentals.
- SDN: Cisco ACI Simulator.
- SDN: OpenStack.
- SDN: install OpenStack with Autopilot (Ubuntu).
- SDN: RDO community, deploy OpenStack on CentOS, Fedora and RHEL.
- SDN: OpenStack sandbox, free way to try OpenStack.
- SDN: RDO TripleO documentation.
- SDN: RDO QuickStart.
- SDN: OpenStack appliance tools.
- SDN: OpenStack NovaImageBuilding.
- SDN: Openstack releases.
- SDN: OpenFlow Archive.
- SDN: OpenFlow & Open Networking Foundation.
- SDN: OpenFlow 1.3 specification.
- SDN: OpenFlow 1.4 specification.
- SDN: Open vSwitch.
- SDN: Indigo - Big Switch.
- SDN: Project Floodlight, OS SDN.
- SDN: OpenDaylight Platform.
- SDN: VMware NSX (/Nicera).
- SDN: NOX Controller.
- SDN: Beacon OpenFlow Controller.
- SDN: Juniper, JunOS SDK.
- SDN: Juniper, Juniper Extension Toolkit (JET)./li>
- SDN: Cisco OnePK.
- SDN: Juniper Contrail SDN solution.
- SDN: IBM SDN VE DOVE.
- CLOUD: Google Cloud Platform.
- SDN: NetFPGA.
- SDN: Cumulus Networks.
- SDN: Arista.
- SDN: RFC 7348, Virtual eXtensible LAN (VXLAN).
- SDN: NVGRE.
- SDN: Stateless Transport Tunneling (STT).
- SDN/SEC: Check Point vSEC.
- SDN/SEC: Trend Micro Deep Security.
- SDN/REL: Segment Routing - An IP/MPLS source-route architecture.
- IDS, IDP, Honeypots:
- X86/x64:
- Storage:
- STOR: Wikipedia on Object Storage.
- STOR: Ceph, unified, distributed storage system.
- STOR: GlusterFS, scalable network file system.
- STOR: Nutanix, Software Defined Storage.
- STOR: VMware vSAN.
- STOR: MS Storage Spaces.
- STOR: RHEL Gluster Storage - Storage Server.
- Cloud:
- Linux:
- Microsoft:
- MS: Security Implications of Windows Access Tokens - A penetration Tester's Guide".
- SELINUX: Wikipedia on SELinux.
- NBT: MS, overview of SMB and CIFS services.
- NBT: Wikipedia on NetBIOS.
- WMI: MS, Windows Management Instrumentation.
- COMMAND: MS Tasklist, display a list of applications and services.
- COMMAND: Netstat, display active TCP ports and connections.
- MOF: using MS MOF files.
- Malware and related:
- MAL: EternalRocks, Github sources, captures and traces.
- MAL/YARA: YARA documentation.
- MAL/YARA: YARA pattern matching for malware researchers.
- MAL/YARA: repository of yara rules (main).
- MAL/YARA: repository of yara rules (github).
- MAL/YARA: Yara Rule Generator.
- MAL/ANA: PEid, dectect common packers, cryptors and compilers for PE files.
- MAL: EvilGrade, perform malicious updates (github).
- MAL: msfvenom = msfpayload + msfencode.
- MAL: how to use msfvenom (github).
- MAL: Wikipedia on Rogueware (security).
- MAL: The business of Rogueware, Panda security.
- MAL: Apple & Mac Defender.
- MAL/BOT: TrendMicro, SDbot.
- MAL/BOT: F-Secure, SDbot.
- MAL/WORM: wikipedia on Nimda.
- ENC: shikata_ga_nai, polymorphic XOR additive feedback encoder.
- ENC: Metasploit Blog: the odd couple: Metasploit and Antivirus Solutions.
- MAL: Heimdal, the ultimate guide to Angler exploit kit for non-technical people.
- MAL: Sophos News, a closer look at the Angler exploit kit.
- MAL: Palo Alto, understanding Angler exploit kit - part 1: exploit kit fundamentals.
- MAL: Wikipedia on Remote Access Trojan.
- MAL/HISTORICAL: Wikipedia on Cult of the Dead Cow.
- MAL/HISTORICAL: BO2K.
- MAL: Wikipedia on Dendroid.
- MAL: MalwareBytes, the state of malware, 2017.
- MAL: Android App stores investigation.
- MAL/TOOL: AVC UnDroid (Beta), submit android apps for analysis.
- MAL/PAPER: John Hopkins, manipulate the led light of camera by malware.
- MAL: Snacksforyourmind, exploring the limits of covert data.
- MAL: Naked Security, Memories of the Chernobyl virus.
- MAL: Wikipedia on Flame.
- Crypto:
- PKI: OWASP, Certificate and public key pinning.
- PKI: SSL pinning for increased app security.
- PKI: Qualys, is http public key pinnign dead?
- PKI: HPKP, HTTP Public Key Pinning.
- PKI: Mozilla, public key pinning.
- PKI/TOOL: Google NoGoToFail, SSL/TLS network testing toolkit (MiTM).
- PKI/VULN: Apple iOS basic constraints.
- PKI/VULN: Apple IOS CVE 2011-0228, basic constraints.
- PKI/IOT: Internet of Sins: million more devices sharing known private keys for HTTPS, SSH admin.
- PKI/IOT: House of Keys: 9 months later ... 40% worse.
- PKI/IOT: House of Keys: industry-wide HTTPS certificate and SSH key reuse endangers millions of devices worldwide.
- PKI: Fox-it on the Diginotar case.
- PKI: Mozilla, comodo certificate issue follow up.
- PKI: comodo, Fraud Incident report.
- PKI: comodo, on the recent RA compromise.
- HASH: Hashcalc for Windows.
- CRYPTO: Wikipedia on S/MIME.
- CRYPTO: Wikipedia on CMS.
- CRYPTO: Public Key Cryptographic Standards (PKCS).
- HASH: Wikipedia on SHA2.
- HASH: NIST on SHA-3.
- HASH: Wikipedia on SHA-3.
- HASH: Wikipedia on Sponge Functions.
- HASH: "we have broken SHA-1" in practice.
- HASH: libray and command line tool to detect SHA-1 collisions in files.
- HASH: Schneier cryptoanalysis of SHA-1.
- HASH: MD5 considered harmful today, creating a rogue CA certificate.
- HASH: MD5 collisions (Selinger).
- HASH/TOOL: Slavasoft Hashcalc.
- HASH: hash collisions - creating a rogue CA certificate (CCC).
- HASH: The Register, boffins bust web authentication with game consoles.
- HTTP: Wikipedia on HTTP/2.
- HTTP: Wikipedia on SPDY (Google).
- SSL/TLS: Datagram Transport Layer Security (UDP) RFC.
- SSL/TLS: The HTTPS Only Standard (US/White House).
- PKI: Let's Encrypt, free, open and automated CA.
- PKI: Let's Encrypt, how does it work?
- SSL/TLS: nice introduction to SSL/TLS, recommended.
- CRYPTOCURRENCY: Map of Coins, map of some of the crypto currencies and forks.
- SSL/TLS: CERTSTREAM, real-time transparency logs.
- SSL/TLS: Cloudflare: introducing TLS 1.3.
- SSL/TLS: TLS 1.3 draft.
- SSL/TLS: Cloudflare: staying on top of TLS attacks.
- SSL/TLS: TLS 1.3 is approved, here's how it could make the entire Internet safer.
- SSL/TLS: cloudflare on TLS 1.3.
- SSL/TLS: ED25519.
- SSL/TLS: ED448-Goldilocks.
- SSL/TLS: ED448 GoldiLocks (SF).
- SSL/TLS: Cloudflare, introducing 0-RTT.
- SSL/TLS: OWASP 2018 - TLS 1.3 by Andy Brodie.
- HASH: Wikipedia on Poly1305.
- CRYPTO: Wikipedia on Galois Counter Mode (GCM).
- CRYPTO: Bypassing HTTP Strict Transport Security (Black Hat), paper.
- CRYPTO: Bypassing HTTP Strict Transport Security (Black Hat), presentation.
- CRYPTO: Breaking SSL using time synchronisation attacks (DEFCON), presentation.
- CRYPTO: Breaking SSL using time synchronisation attacks, Youtube video (DEFCON).
- CRYPTO: Breaking out HSTS (and HPKP) on Firefox, IE/Edge and (Possibly) Chrome.
- CRYPTO: New tricks for defeating SSL in practice, Moxie, Black Hat.
- CRYPTO: zero-config tool to make locally trusted development certificates.
- CRYPTO: Tradeoff Cryptanalysis of Memory-Hard Functions.
- CRYPTO: Password hashing competition, and our recommendation for hashing passwords: Argon2.
- CRYPTO: ARGON2.
- CRYPTO: CCMiner (GPU) on Github.
- CRYPTO: LastPass: how PBKDF2 strengthens your master password.
- CRYPTO: PBKDF2 calculator.
- CRYPTO BCrypt.
- CRYPTO: BCrypt calculator.
- CRYPTO: BitCoinWiki: Scrypt.
- CRYPTO: Argon2 in browser.
- CRYPTO: OWASP, password storage cheat sheet.
- CRYPTO: Australian Academy of Science: Quantum Computers Explained.
- CRYPTO: IBM Dr. Talia Gershon explains Quantum Computers.
- Pentesting:
- PEN: PTES, Penetration Testing Standard.
- PEN: PTES, technical standard.
- PEN: a simple guide to successful penetration testing.
- PEN: Mitre, ATT&CK, Adversarial Tactics, Techniques and Common Knowledge.
- PEN: Mitre, pre-ATT&CK.
- PEN: Mitre, attack navigator.
- PEN: Mitre, all attack techniques.
- End user:
- END: Netcraft Toolbar, report/get information on dangerous sites.
- END: Have I been pwned by Troy Hunt, verify password compromise.
- END: Belgium, Safe On Web.
- CERT/CC: Who needs to exploit vulnerabilities when you have macros?
- END: No More Ransom.org, might help with decryption.
- END: identity theft resource center.
- END: Flexera Personal Software Inspector (formerly Secunia PSI).
- END: VirusTotal, analyze suspicious files and URLs.
- END/TOR: Tails, privacy oriented operating system.
- END: Microsoft Security TechCenter, security update guide.
- END: Use OpenDNS.
- END: Identity Theft Resource Center.
- END: use the free DNS filter from Cisco/OpenDNS.
- END: use Google DNS for enhanced speed (no filters).
- END: (Dutch) Meldpunt België: consumer/enterprise rights, fraud, deception, ...
- END: mailinator.com, free, disposable (and public) mailboxes to fight spam.
- END: Punycode converter, IDN converter, ...
- END: password manager, LastPass.
- END: KeePass.
- END: Phishing.org.
- END: How "HTTPS works", in a comic.
- END: urlscan.io - a sandbox of the web - service to scan and analyse websites: act as a regular user and record activity.
- END: TEDX, James Veitch, This is what happens when you reply to spam email.
- Artificial Intelligence
- AI: Seeing is Deceiving: The rise of fake media and how to fight back (AI Conference, 2019 (NY)).
- AI: SIGGRAPH 2019, Text-based editing of talking-head video.
- Programming:
- PROG: Python, virtualenvs.
- PROG: Python, code with MU - a simple Python editor for beginner programmers.
- PROG: the Hitchhiker's Guide to Python!
- PROG: PY2, installating Python modules.
- PROG: Python for Everybody.
- PROG: Invent with Python, free books.
- PROG: Datacamp, learnpython.org.
- PROG: Code Academy, learn to code interactively for free.
- PROG: MIT 6.00SC Introduction to Computer Science and Programming.
- PROG: Python Course (P2 and P3).
- PROG: free books (IOT, Programming, Security, ...) by O'Reilly.
- PROG: O'Reilly, Python in Education (free).
- PROG: O'Reilly, functional programming in Python (free).
- PROG: Official Python 3 tutorial.
- PROG: the non-programmers tutorial for python 2.6.
- PROG: New Boston, Python programming tutorials.
- PROG: Python from Scratch.
- PROG: learn python the hard way.
- PROG: Green Tea Press, how to think like a computer scientist (free).
- PROG: PyGame.
- PROG: Microsoft Make Code - hands on computing education.
- VAR: ASCII chart.
- JUP: What is Jupyter?.
- JUP: Jupyter Notebook for beginners: a tutorial.
- Fraud:
- FRAUD: Tom Kemp, CEO Fraud: a first hand encounter.
- PHISH: utility that uses machine learning to detect phishing domains from the Certificate Transparency Log Network.
- SFX:
- MS Powershell:
- Online learning:
- LEARN: Media Archive of the Chaos Computer Club (CCC).
- VBLOG: Cisco TechWise TV.
- YOUTUBE: Cisco.
- PYTHON: University of Waterloo (.CA), Python from scratch.
- PROGRAM: University of Waterloo (.CA), Open Computer Science.
- PROGRAM: Computer Science Circles.
- PROGRAM: PythonLearn.
- PROGRAM: official Python website.
- PROGRAM: run Python 3 in browser.
- PLAY: Cisco Devnet Sandbox.
- PLAY: VMware HOL Labs.
- PLAY: Microsoft Server 2016 Virtual Labs.
- PLAY: Cisco Dcloud Labs.
- PLAY: Mininet, an instant virtual network on your machine.
- LEARN: Media CCC.
- LEARN: F5 free courses.
- LEARN: Splunk 6.X fundamentals (free).
- LEARN: HTML & CSS.
- LEARN: LiveOverflow (Youtube) explanation on the art of memory attacks and exploits.
- LEARN: SecurityTube.
- LEARN: O'Reilly, Safari Books Online (video, courses, books, prepguides, ...).
- LEARN: LinkedIn Learning (mostly video).
- LEARN: Cybrary, free and open source learning.
- LEARN: MOOC, Coursera.
- LEARN: TED.
- LEARN: MOOC, MOOC.ORG.
- LEARN: MOOC, EDX.
- LEARN: MOOC, Standford Online.
- LEARN: MOOC, Khan Academy.
- LEARN: MOOC, Udacity.
- LEARN: MOOC, FutureLearn.
- LEARN: MOOC, OpenClassRooms.
- LEARN: MOOC, Open2Study.
- LEARN: MOOC, Udemy.
- LEARN: MOOC, MOOC LIST.
- LEARN: The Cisco Learning Network Store.
- LEARN: DataCamp - data science online.
- LEARN: Open Culture.
- LEARN: MIT Open CourseWare.
- LEARN: Class Central, free online learning.
- LEARN: Cisco, Virtual Internet Routing Lab (VIRL).
- LEARN: Cisco Packet Tracer, a free network and IoT simulation and visualization tool.
- LEARN: MS Learning Portal.
- LEARN: Plural Sight.
- YOUTUBE: Metasploit Rapid7 videos.
- LEARN: Net2Plan, the open-source network planner.
- LEARN: Cisco On-Demand Library (Cisco Live).
- LEARN: O'Reilly Radar Podcasts.
- LEARN: NICE, National Initiative for CyberSecurity Education NICE).
- LEARN: Amazon Re:Invent.
- LEARN: The TCP/IP Guide.
- LEARN: FutureProof from Microsoft.
- LEARN: Executive Level Courses.
- LEARN: Free Cuckoo's Egg course by Chris Sanders.
- Certification stuff:
- CISSP: ISC2 CISSP list of self study resources.
- CISSP: ISC2 CISSP exam outline (valid to the end of 2017.
- CISSP: Cybrary ISC2 CISSP Course.
- Official CISSP ISC2 Study Guide and Practice Tests Kit (Sybex).
- Official ISC2 Guide to the CISSP CBK, ISC2 Press.
- Fortinet, training.
- Various security topics:
- SEC: Wikipedia on MAC (Mandatory Access Control).
- SEC: Wikipedia on DAC (Discretionary Access Control).
- Conferences and more:
- CONF: USENIX conferences.
- CONF: DEF CON.
- CONF: Black Hat.
- CONF: Chaos Computer Club (CCC).
- CONF: BruCON.
- CONF: HACK.LU.
- CONF: CANSECWEST.
- CONF: SecAppDev.
- CONF: DEEPSEC.
- CONF: DEFCON, YouTube channel.
- CONF: Security B Sides.
- CONF: Security B Sides Delaware, YouTube Channel.
- Standards, compliancy, ...:
- Firewalls, DLP, ...:
- DLP: PTP-RAT, RDP data leakage.
- DLP: Pen Test Partners, exfiltration by encoding data in pixel colour values.
- OSINT:
- OSINT: Eleven Paths, Fingerprinting Organizations with collected archives.
- Social Engineering Toolkit.
- SIGINT:
- Laws, organisations, standards, guides, ...:
- LAW: US - S.1869 - Federal Cybersecurity Enhancement Act of 2016.
- LAW: US - Wikipedia on the US Computer Fraud and Abuse Act.
- LAW: US - Wikipedia on the US PATRIOT act.
- TERROR: EU - Council of Europe, combating terrorism.
- TERROR: EU - OCSE, countering the use of the Internet for terrorist purposes.
- LAW: BE - Wet van 28 november 2000 inzake informaticacriminaliteit.
- LAW: BE - Wikipedia on "Wet inzake informaticacriminaliteit.
- LAW: BE - government, computercrime.
- LAW: BE - bestuurlijke aanpak in de bestrijding van criminaliteit.
- LAW: EU Convention on CyberCrime CETS number 185.
- ORG: European Committee on Crime Problems.
- ORG: EU, Cybercrime Convention Committee.
- LAW: EU Directive on Security of Network and Information Systems.
- LAW: cybersecurityintelligence.com on GDPR.
- LAW: itgovernance.co.uk on GDPR.
- STND: itgovernance.co.uk on ISO22301 BCS.
- ORG: UK National Cyber Security Centre, part of the GCHQ.
- NIST: Workforce Management Guidebook.
- Cyber Crime:
- 2017 * MS: Microsoft giving away loads of ebooks.
- 2016 * : The Hacker Playbook 2.
- 2016 * PACKT: Penetration testing: a survival guide.
- 2016 * PACKT: Penetration testing, github resources.
- Framework:
- Routing:
- APNIC: The Internet routing Registry (IRR).
- APNIC: Resource Public Key Infrastructure (RPKI).
- Cloudflare: RPKI - The required cryptographic upgrade to BGP routing.
- Cloudflare: MANRS, Mutually Agreed Norms for Routing Security.
- YouTube: MANRS.
- Mobile:
- MOB: Breaking LTE on Layer Two.
- MOB: Paper, Breaking LTE on Layer Two.
- MOB: Shattered Trust: When replacement smartphone components attack.
- GPS: All Your GPS Are Belong To Us.
- MOB: P2P-ADB, Phone to Phone Android Debug Bridge.
- IoT:
- IOT: Check Point Research, Remote Code Execution on a fax machine.
- IOT: Check Point Research, UltraHack - Ultrasound attack.
- Machine Learning:
- Interesting video's and related:
- [YOUTUBE * BLOCKCHAIN] Blockchain: distributed trust (Bart Preneel).
- [ASCIICEMA * SHODAN] Analysing Public SMB exposure using the Shodan CLI.
- [YOUTUBE * ANDROID] Shattered Trust: When replacement smartphone components attack.
- Big Data:
- General articles and reads, security:
- [07/2019 * PRIVACY] Forbes, the encryption debate is over - dead at the hands of facebook.
- [07/2019 * OPS] The Register, Operation Desert Sh!tstorm: routine test shoots down military's top-secret internets.
- [07/2019 * SLACK] The Register, 2015 database hack is the terrible gift that keeps giving for Slack.
- [07/2019 * CNN] FaceApp's viral success proves we will never take our digital privacy seriously.
- [07/2019 * APIS] The Register, patch now before you get your NAS kicked: Iomega storage boxes leave millions of files open to the Internet.
- [07/2019 * IDOR] The Register, Amadeus! Amadeus! Pwn me Amadeus! Airline check-in bug may have exposed all y'all boarding passes to spies.
- [07/2019 * C++] The Register, Rust in Peace: memory bugs in C and C++ code cause security issues so Microsoft is considering alternatives once again.
- [07/2019 * LIBRA] Libra, official Libra White Paper.
- [07/2019 * LIBRA] WIRED, The ambitious plan behind facebook's cryptocurrency, Libra.
- [06/2019 * WETRANSFER] Wetransfer, update security notice.
- [06/2019 * BGP] MANRS, large European routing leak sends traffic through China telecom.
- [06/2019 * BGP] The Register, BGP super-blunder: how Verizon today sparked a "cascading catastrophic failure" that knackered Cloudflare, Amazon, etc."
- [06/2019 * VIM] Sophos, VIM devs fix system pwning text editor bug.
- [06/2019 * VIM] Medium, Exploit PoC: Linux command execution on Vim/Neovim vulnerability (CVE-2019-12735).
- [06/2019 * BGP] Cloudflare, How Verizon and a BGP optimizer knocked large parts of the Internet Offline today.
- [06/2019 * ML] The Verge, AI Deepfakes are now as simple as typing whatever you want your subject to say.
- [06/2019 * RANSOM] VRT NWS, Military secrets hacked in Zaventem (Asco).
- "[06/2019 * RANSOM] RTBF, L'entreprise ASCO paralysée par une cyberattaque, les activités mondiales à l'arrêt.
- [06/2019 * RANSOM] De Tijd, luchtvaartbedrijf Asco gehackt.
- [05/2019 * 0DAY] Security Boulevard, Sandboxescaper drops four Windows Zero-Days.
- [05/2019 * SIMPORT] CoinSpice, BitGo Engineer's Coinbase account hacked for more than $100K: "Expensive Lesson".
- [05/2019 * HUAWEI] Bloomberg, Huawei supply freeze points to US - China cold war.
- [05/2019 * LINUX] Bleeping Computer, Linux Kernel prior to 508 vulnerable to remote code execution.
- [05/2019 * HUAWEI] The Register, Trump declares national emergency, starts ball rolling to boot Huawei out of ALL US networks.
- [04/2019 * MALWARE] Tweakers, Security-onderzoeker die WannaCry stopte, bekent schuld over eigen malware.
- [04/2019 * Cisco] TALOS, Hiding in Plain Sight.
- [04/2019 * DDoS] NetScout, The Rise and Fall of Memcached.
- [04/2019 * INTEL] Eweek, new Intel Chip Bug can expose all data on a computer to hackers.
- [02/2019 * BIOMETRICS] Tweakers.net: vingerafdrukken op Belgische identiteitskaart onnodig en onveilig.
- [02/2019 * INNET] The Register: Russia preps to turn its internet into an intranet if West opens Cyber-Fire.
- [02/2019 * TLS] SC Magazine UK, TLS 1.3 vulnerability enables hackers to eavesdrop on encrypted traffic.
- [02/2019 * BREACH] ArsTechnica, "Catastrophic" hack on email provider destroys almost two decades of data.
- [02/2019 * WEB] Wires, Google takes its first steps toward killing the URL.
- [01/2019 * HASH] Medium, password hashing: scrypt, bcrypt and ARGON2.
- [01/2019 * CRYPTO] ArsTechnica, Digital Exchange loses $137 million as founder takes password to the grave.
- [01/2019 * IOT] Tweakers.net, Europese Commissie laat onveilig gps-horloge voor kinderen van de markt halen.
- [01/2019 * QUANTUM] Enterprises Project: Quantum Computing and security: 5 glooming questions.
- [01/2019 * HUAWEI] Wired, Huawei's many troubles: bans, alleged spieds, and backdoors.
- [01/2019 * PASSWORDS] Troy Hunt, The 773 Million Record "Collection #1" Data Breach.
- [01/2019 * FACEBOOK] Pew Research Center, Facebook Algorithms and Personal Data.
- [01/2019 * QUANTUM] IBTimes, IBM's Quantum computer first in the world to leave research labs: Unbelievable Facts.
- [01/2019 * FORENSICS] ZDNet, Hancom GMD, Explosion in digital evidence coming thanks to IoT and 5G.
- [12/2018 * EU] European Commission: EU negotiators agree on strengthening Europe's cybersecurity.
- [12/2018 * HUAWEI] De Tijd, België voert onderzoek naar Chinese Huawei.
- [12/2018 * FBI] ZDNet: ACLU wants court to release documents on the US'attempt at backdooring Facebook Messenger.
- [12/2018 * GCHQ] The Register: GCHQ pushes for "virtual crocodile clips" on chat apps - the ability to silently slip into private encrypted comms".
- [11/2018 * DRONE] VTM Nieuws: Hackers ontdekken veiligheidslek (XSS) by drones.
- [11/2018 * DRONE] TechCrunch: Security Flaw in DJI's website and apps exposed accounts to hackers and drone live feeds.
- [11/2018 * PHISH] Cisco TALOS, Persian Stalker pillages Iranian users of Instagram and Telegram.
- [11/2018 * CPU] Ars Technica, Intel CPUs fall to new hyperthreading exploit that pilfers crypto keys.
- [10/2018 * ML/EDU] Harvert Business Review, The Chairman of Nokia on Ensuring Every Employee Has a Basic Understanding of Machine Learning - Including Him.
- [09/2018 * NSA] ZDNet, Ex-NSA employee gets 5.5 years in prison for taking home classified info.
- [09/2018 * AWARENESS] Medium, how a password changed my life.
- [09/2018 * NSA] De Tijd, Brise spionage bij Proximus op tafel regering.
- [09/2018 * CISCO] Cisco IOS XE Software Static Credential Vulnerability.
- [08/2018 * SNIFF] BleepingComputer, SonarSnoop Acoustic Side-Channel Attack can stel touchscreen interactions.
- [08/2018 * SNIFF] BleepingComputer, New Side-Channel Attack uses microphone to read screen content.
- [08/2018 * APPLE] Forbes, hackers are exposing an apple MAC Weakness in the Middle East Espionage.
- [08/2018 * IOT] Philips cardiovascular software found to contain privilege escalation, code execution bugs.
- [08/2018 * SOCIAL] Check Point Research, FakesApp: a vulnerability in WhatsApp.
- [08/2018 * USB] BBC News, This rigged charger can hijack your new laptop.
- [08/2018 * MACOSX] The mouse is mightier than the sword, Patrick Wardle on CVE-2017-7150.
- [07/2018 * MALWARE] Sophos: Red Alert 2.0: Android Trojan targets security-seekers.
- [07/208 * RANSOM] Ransomware Infection Cripples Shipping Giant COSCO's American Network.
- [07/2018 * IOT] The Register, I feel like my IoT enabled vacuum cleaner is spying on me.
- [07/2018 * Linux] Palo Alto, analysis of the DHCP client script code execution vulnerability (CVE-2018-1111).
- [07/2018 * ANDROID]l IBM SEC INT, Anubis Strikes again: mobile malware continues to plague users in official app stores.
- [07/2018 * SPOOF] Bleeping Computer, Researchers mount successful GPS spoofing attack against road navigation systems.
- [07/2018 * PENTEST] De Tijd, Nationale Bank gaat banken hacken.
- [07/2018 * SPECTRE] The Register, Google's Ghost Busters: we can scare off Spectre haunting Chrome tabs.
- [07/2018 * CPU] The Register, Another data-leaking spectre CPU flaw.
- [07/2018 * BREACH] The Register, US MIL manuals hawked on dark web after files left rattling in insecure FTP server.
- [07/2018 * BREACH] Recorded Future, Military Reaper Drone Documents Leaked on the Dark Web.
- [07/2018 * MALWARE] Cryptocurrency users on Discord and Slack hit by MacOS Malware.
- [07/2018 * PRIVACY] VanityFair, Tim Berners Lee - the man who created the World Wide Web has some regrets.
- [07/2018 * AngularJS] FinnWea, Stealing passwords from McDonald's users.
- [06/2018 * WIFI] The Register: WPA3 is the magic number? Protocol refresh promises tighter Wi-Fi security.
- [04/2018 * PHISH] Medium, an expertly crafted crypto phishing.
- [05/2018 * VULNERABILITY] The Register, Red Hat admin? Get off twitter and patch this DHCP client bug.
- [04/2018 * FINTECH] O'Reilly Radar, Simon Moss on Using Artificial Intelligence to fight financial crimes.
- [04/2018 * MALWARE] ArsTechnica, Intel & MS to use GPU to scan memory for malware.
- [04/2018 * VULN] Cisco TALOS, Critical infrastructure at risk: advanced actors target smart install client.
- [03/2018 * VULN] The Register, MS Windows 7 Meltdown fixes from January, February made PCS MORE INSECURE.
- [03/2018 * EXPLOIT] The Register, exploit kit development has gone sh$t...ever since Adobe Flash was kicked to the curb.
- [03/2018 * EDITORS] ThreatPost, security risk in extensible text editors enable hackers to abuse plugins and escalate privileges.
- [03/2018 * SE] RM IT, iOS camera QR code URL parser bug.
- [03/2018 * SE] The Register, how a QR code can fool iOS 11 camera app into opening evil.com rather than nice.co.uk.
- [03/2018 * FRAUD] Febelfin, Fraudsters seek out social environment of adolescents.
- [03/2018 * PRIVACY] NYTimes: Facebook's Surveillance Machine (Cambridge Analytica).
- [03/2018 * DDOS] Wired, Github survived the biggest ddos attack ever recorded.
- [02/2018 * QUANTUM] MIT Technology Review: serious quantum computers are finally here. What are we going to do with them?
- [02/2018 * CPU] The Register: Hate to ruin your day, but ... Boffins cook up fresh Meltdown, Spectre CPU design flaw exploits.
- [02/2018 * NSA] The Verge: don't use Huawei phones, say heads of FBI, CIA and NSA.
- [02/2018 * PRIVESC] The Register, Ghost in the DCL shell: OpenVMS touted as ultra reliable, had a local root hole for 30 years.
- [02/2018 * TOOL] EvilSocket, All hail bettercap 2.0, one tool to rule them all.
- [02/2018 * DDOS] Tweaker.net, een ddos'er betrapt.
- [02/2018 * CRYPTO] BBC.com, Russian nuclear scientists arrested for 'Bitcoin mining plot'.
- [01/2018 * DDOS] NRC.NL, ABN AMRO en ING opnieuw doelwit van DDoS-aanvallen.
- [01/2018 * HARDWARE] Krebs on Security, first "jackpotting" attack hits U.S. ATMs.
- [01/2018 * DDOS] Wired, Github survived the biggest DDoS attack ever recorded.
- [01/2018 * FOR] Darkreading, Hackers who disabled police cameras prior to Trump inauguaration left trail of clues.
- [01/2018 * OSINT] Wired, Strava heat map and the end of secrets.
- [01/2018 * OSINT] The Verge, Strava fitness tracker heat map reveals location of military bases.
- [01/2018 * MALWARE] The Register, after NotPetya, Maersk replaced everything.
- [12/2017 * AWS] The Register, Good News: unsecured S3 bucket discovery just got easier.
- [12/2017 * AWS] The Register, This week in 'Bungles in the AWS S3 privacy jungles', we preset Alteryx and 123 million households exposed.
- [01/2018 * MALWARE] ZDNet, Maersk forced to reinstall 4000 servers and 45000 pcs due to NotPetya attack.
- [11/2017 * AWS] The Register, US intelligence blabs classified Linux VM to world via leaky S3 silo.
- [11/2017 * MITM] Bleeping Computer: misconfigured Amazon S3 buckets expose users to stealthy MITM attacks.
- [11/2017 * MALWARE] Threatpost, new fileless attack using DNS queries to carry out powershell commands.
- [11/2017 * AWS] The Register, massive US military social media spying archive left wide open in AWS S3 buckets.
- [11/2017 * APPLE] ArsTechnica: MacOS bug lets you log in as admin with no password required.
- [11/2017 * AWS] The Register, Amazon's answer to all those leaky AWS S3 buckets: A dashboard warning light.
- [11/2017 * MALWARE] ZDNet, fileless attacks surge in 2017 and security solutions are not stopping them.
- [11/2017 * LAW] ZDNet, Trump administration releases secret rules on disclosing security flaws.
- [11/2017 * APT] ZDNet: DHS FBI describe North Korea use of FALLCHILL malware.
- [11/2017 * PHISH] ZDNet - how criminals clear your stolen iPhone for resale.
- [11/2017 * PENTEST] WIRED: He perfected a password-hacking tool - then the Russians came calling.
- [11/2017 * AWS] AWS News Blog: new Amazon S3 encryption and security features.
- [11/2017 * FUZZING] ZDNet: Linus Torvalds says targeted fuzzing is improving Linux security.
- [11/2017 * CRYPTO] MIT: Quantum computers pose imminent trheat to bitcoin security.
- [11/2017 * CRYPTO] MIT: Quantum breakthrough heralds new generation of perfectly secure messaging.
- [10/2017 * IOT] Wired, Reaper IOT botnet infected million networks.
- [10/2017 * MALWARE] BitDefender Labs, Bad Rabbit Ransomware strikes Ukraine, likely related to GoldenEye.
- [10/2017 * VULNERABILITY] The Register, Dnsmasq and the seven flaws: patch these nasty remote-control holes.
- [10/2017 * MacOS] The Register: dumb bug of the week: Apple's macOS reveals your encrypted drive's password in the hint box.
- [10/2017 * AWS] The Register, Et tu Accenture? Then fall S3er: consultancy leaks private keys, emails and more online.
- [10/2017 * NSA] Ars Technica: Russia reportedly stole NSA secrets with help of Kaspersky - what we know now.
- [10/2017 * NSA] Wall Street Journal: Russian Hackers stole NSA data on U.S. Cyber Defense.
- [09/2017 * DHS] US Department on Homeland Security: Directive 17-01 on Kaspersky.
- [09/2017 * DOS] CNN: Earth dodges a cosmic bullet -- for now.
- [09/2017 * MALWARE] Bleeping Computer: CCleaner compromised to distribute malware for almost a month.
- [09/2017 * MALWARE] Cisco Talos: CCleanup: a vast number of machines at risk.
- [06/2017 * MALWARE] Piriform Blog: Security notification for CCleaner.
- [09/2017 * BLUETOOTH] ArsTechnica: Billions of devices imperiled by new clickless Bluetooth attack.
- [08/2017 * MALWARE] The Register: Britisch snoops at GCHQ knew FBI as going to arrest Marcus Hutchins.
- [08/2017 * BGP] BGPMON: BGP leak causing Internet outages in Japan and beyond.
- [08/2017 * BGP] The Register: Google routing blunder sent Japan's Internet dark on Friday.
- [08/2017 * SNOWDEN]SecurityAffairs: a new batch of documents leaked by snowden has revealed a US facility in Australia for covertly monitoring communications and supporting drone missions.
- [08/2017 * BE] De Morgen: Belgische Bedrijfven hebben Cyberkopzorgen.
- [08/2017 * PHY] Bleeping Computer: USB devices vulnerable to crosstalk data leaks.
- [08/2017 * PHY] The Register: Infosec eggheads rig USB desk lamp to leak passwords via Bluetooth.
- [08/2017 * AWS] The Register: Don't panic, Chicago, but an AWS S3 config blunder exposed 1.8 million vote records.
- [08/2017 * BREACH] Reuters: HBO says probe of hack is ongoing.
- [08/2017 * BREACH] Future Tense: The HBO hackers are demanding $7.5 million to stop leaking Game of Thrones.
- [08/2017 * BREACH] The Verge: HBO hackers leak Game of Thrones star's phone numbers and addresses.
- [08/2017 * SEC] The Register: Salesforce sacks two top security engineers for their DEF CON talk.
- [08/2017 * ANDROID] The Register: it's August 2017 and your Android gear can be pwned by, oh look, just patch the things.
- [08/2017 * IoT] The Register: firmware update blunder bricks hundreds of home 'smart' locks.
- [07/2017 * AWS] The Register: 14 million Verizon subscribers' details leak from crappily configured AWS S3 data store.
- [07/2017 * FRAUD] The Verge: a dark web marketplace is down and users suspect foul paly.
- [07/2017 * FRAUD] Wired, the biggest dark web takedown yet sens black markets reeling.
- [07/2017 * MALWARE] OSX/Dok malware hits Macs; bypasses Apple' Gatekeeper.
- [07/2017 * FRAUD] Politie.NL: underground Hansa Market taken over and shut down.
- [07/2017 * FRAUD] The Verge, Dark Web drug marketplace AlphaBay was shut down by law enforcement.
- [07/2017 * MS] ThreatPost: Windows SMB Zero Day to be disclosed during DEF CON.
- [07/2017 * MS] The Register: Microsoft won't patch SMB flaw that only an idiot would expose.
- [07/2017 * BREACH] The Register: Game of Pwns: hackers invade HBO, 'leak Game of Thrones script'."
- [07/2017 * CRACK] The Telegraph UK: 'brute force' cyber attack on parliament compromised up to 90 email accounts.
- [07/2017 * MALWARE] Wired: latest ransomware hackers didn't make wannacry's mistakes.
- [07/2017 * FRAUD] Reuters, Germin firms lost millions of euros in 'CEO Fraud' scam: BSI.
- [07/2017 * AWS] The Register, US voter info stored on wide-open cloud box, thanks to bungling Republican contractor.
- [07/2016 * MALWARE] Wired: the botnet that broke the internet isn't going away.
- [06/2017 * DoS] The Register: management bug can crash Cisco IOS, IOS XE.
- [06/2017 * PII] Ars Technica: how a few yellow dots burned the Intercept's NSA leaker.
- [06/2017 * MALWARE] The Register, How to Pwn phones with shady replacement parts.
- [06/2017 * PII] National Post: 'Colour printers spy on you': barely visible yellow dots lead to arrest of Reality Winner alleged NSA leaker.
- [06/2017 * PII] Errata Security: how The Intercept outed Reality Winner.
- [05/2017 * MALWARE] The Guardian, what is WannaCry ransomware and why is it attacking global computers?
- [05/2017 * MALWARE] IBM XFORCE: Eternalrocks Worm.
- [04/2017 * MALWARE] The Register: Script kiddies pwn 1000s of Windows boxes using leaked NSA hack tools.
- [**/2017 * PHISH] Infosecurity Magazine: global banks hit by watering hole blitz.
- [02/2017 * MALWARE] Cisco TALOS, covert channels and poor decisions: the tale of DNSMessenger.
- [03/2017 * PENTEST] Threatpost, hackers take down reader, safari, edge, ubuntu linux at pwn2own 2017.
- [02/2017 * PENTEST]: Rapid7, under the hoodie.
- [02/2017 * CISCO] The Register, Cisco says Smart Install is not a bug, not a vuln, releases blocker anyway.
- [02/2017 * SQLi] HelpNetSecurity, hacker breached 60+ unis, govt agencies via SQL injection.
- [01/2017 * BOTNET] TechnologyReview.com: cybersecurity experts uncover dormant botnet of 350.000 twitter accounts.
- [01/2017 * LAW] Wolters Kluwer, wetgeving bijzondere opsporingsmethoden krijgt grondige update.
- [01/2017 * REPORT]: Shodan: Heartbleed Report (2017-01)(CVE-2014-0160).
- [01/2017 * MongoDB] DarkNet: MongoDB Ransack - over 33.000 databases hacked.
- [12/2016 * DDoS] The Register: DDoS script kiddies are also ... actual kiddies, Europol arrests reveal.
- [12/2016 * DEV] The Register, Macbook seized or stolen? But you've set a FileVault password, right? Ha, it's useless.
- [11/2016 * MALWARE] The Register, Mirai scan tool unleashed.
- [11/2016 * LINUX] The Hacker News, this hack gives Linux root shell just by pressing "ENTER" for 70 seconds.
- [10/2016 * LAW] Knack, ethisch hacking in België: illegaal, maar het tij keert.
- [10/2016 * ANDROID] Ars Technica: Android phones rooted by "most serious" Linux esclation bug ever.
- [10/2016 * PKI] Chrome: Announcement: Requiring Certificate Transparency in 2017.
- [10/2016 * DDoS] The Verge: Denial-of-Service attacks are shutting down major websites across the Internet.
- [09/2016 * IoT] The Register: Internet of Sins, million more devices sharing known private keys for HTTPS, SSH admin.
- [09/2016 * NEWS] Yahoo! Finance: An important message to Yahoo users on security.
- [08/2016 * PROXY] Computerworld: attackers use rogue proxies to hijack https traffic.
- [08/2016 * PROXY] Computerworld: disable WPAD now or have your accounts and private data compromised.
- [05/2016 * MALWARE] The Atlantic: the computer virus that haunted early AIDS researchers.
- [04/2016 * SOCIAL] Ars Technica: it's 2016, so why is the world still falling for Office macro malware?
- [04/2016 * FIREWALL] SC Media: "Multigrain" variant of POS malware crops up; uses DNS tunneling to steal data.
- [04/2016 * MONGODB] DarkNet: BeautifulPeople.com leak exposes 1.1M extermely private records.
- [04/2016 * SOCIAL] NakedSecurity: Almost half of dropped USB sticks will get plugged in.
- [04/2016 * SOCIAL] Trend Micro: Macro Malware: Here's what you need to know in 2016.
- [04/2016 * MALWARE] FireEye: MULTIGRAIN - PoS attackers make an unhealthy addition to the Pantry.
- [03/2016 * OS] Sophos: millions of people are still running Windows XP.
- [03/2016 * PENTEST] SecurityWeek: lateral movement, when cyber attacks go sideways.
- [03/2016 * ANDROID] HelpNetSecurity: malicious Chrome update actively targeting Android users.
- [02/2016 * MALWARE] The Register: medical superbugs: two german hospitals hit with ransomware.
- [02/2016 * SE] Symantec Blog: Russian bank employees received fake job offers in targeted email attack.
- [02/2016 * APT] Collaborative operation Blockbuster aims to send Lazarus back to the dead.
- [02/2016 * MALWARE] Los Angeles Times: Hollywood hospital pays $71,000 in bitcoin to hackers; FBI investigating.
- [01/2016 * NSA] PcWorld: the ultra-secure Tails OS beloved by Edward Snowden gets a major upgrade.
- [12/2015 * MARIANAS] Engadget: the myth of the marianas web, the darkest corner of the Internet.
- [10/2015 * NSA] Ars Technica, how the NSA can break trillions of encrypte web and vpn connections.
- [06/2015 * VOIP] The Register: Phone hacking blitz hammers UK.biz's poor VoIP handsets.
- [05/2015 * JUNIPER] Rapid7: CVE-2015-7755: Juniper ScreenOS Authentication Backdoor.
- [04/2015 * NSA] Fox-IT: deep dive into QUANTUM INSERT.
- [04/2015 * NSA] Wired: how to detect sneaky NSA QUANTUM INSERT attacks.
- [04/2015 * NSA] Wired: researchers uncover method to detect NSA quantum insert hacks.
- [03/2015 * MALWARE] TALOS: Angler lurking in the domain shadows.
- [03/2015 * MALWARE] MalwareBytes: domain shadowing.
- [03/2015 * DNS] Cloudflare, deprecating the DNS ANY meta-query type.
- [03/2015 * MALWARE] Threatpost: domain shadowing latest angler exploit kit evasion technique with a twist.
- [12/2014 * TOR] Wired: the FBI used the web's favorite hacking tool to unmask Tor users.
- [11/2014 * STUXNET] Wired: an unprecedented look at Stuxnet, the world's first digital weapon.
- [11/2014 * MITM] Zimperium discovers full icmp redirect attacks in the wild.
- [09/2014 * SHELLSHOCK] Lcamtuf: Quick notes about the bash bug, it's impact, and the fixes so far.
- [09/2014 * SHELLSHOCK] The Register: "SMASH the Bash bug! Apple and Red Hat scramble for patch batches."
- [09/2014 * MALWARE] PCWorld: hackers make drive-by download attacks stealthier with fileless infections.
- [07/2014 * NSA] Das Erste: Panorama, NSA targets the privacy-conscious.
- [07/2014 * NSA] Schneier on Security: NSA targets the privacy-conscious for surveillance.
- [07/2014 * MALWARE] Virus Bulletin: VBA is not dead!
- [05/2014 * MALWARE] Ars Technica: photos of an NSA "upgrade" factory show Cisco router getting implant.
- [04/2014 * NSA] INFOSEC: Turbine Quantum implants arsenal.
- [04/2014 * NSA] Wired: Out in the open: inside the operating system Edward Snowden used to evade the NSA.
- [03/2014 * NSA] ZDNET: Linux Tails: het OS waarmee Snowden de NSA te slim af was.
- [03/2014 * NSA] Wired: a clos look at the NSA most powerful internet attack tool.
- [03/2014 * NTML] Security Affairs, Experts at Imperva have illustrated how to exploit NTML flaws to conduct a Windows folder poisoning attack..."
- [03/20134 * DNS] Cisco Umbrella, DNS Amplification Attacks.
- [12/2013 * NSA] Der Spiegel: The NSA uses a powerful toolbox in effort to spy on global networks.
- [12/2013 * DDOS] Symentec Blog: hackers spend christmas breack launching large scale NTP-Reflection attacks.
- [08/2013 * NSA] Der Spiegel: Germany is both a partner to and a target of NSA surveillance.
- [09/2013 * MITM] Schneier on security: new NSA leak show MITM attacks against major Internet services.
- [03/2013 * AWS] Rapid7 Blog, There's a hole in 1.951 Amazon S3 buckets.
- [01/2013 * VULN] PWN2HACK: facebug bug allows password reset.
- [11/2012 * MALWARE] The Register: crooks inject malicious Java applet into FOREX trading website".
- [11/2012 * PKI] SecurityWeek: Hacker had total control over DigiNotar servers, Report.
- [10/2012 * HASH] NIST: NIST selects winner of Secure Hash Algorithm (SHA-3) competition.
- [06/2012 * HASH]Ars Technica: SHA1 crypto algorithm underpinning Internet security could fall by 2018.
- [05/2012 * MALWARE] Ars Technica, Flame malware hijacks Windows update to spread from PC to PC.
- [03/2012 * PII] Wired: Oops! Did Vice just give away John McAfee's location with photo metadata?
- [04/2012 * MALWARE] Ars Technica: "Flame" malware was signed by rogue Microsoft certificate.
- [03/2012 * OSINT] LiveScience, insurgents destroyed helicopters found in online photos.
- [03/2012 * MITB] BBC Technology, hackers outwit online banking identity security ssytems.
- [09/2011 * PKI] Arstechnica: Comodo hacker, I hacked Diginotar too...
- [07/2011 * BACKDOOR] ScaryBeasts: Alert, vsftpd download backdoored.
- [07/2011 * APPLE] PCWorld, a hacker speaks: how malware might blow up your laptop.
- [07/2011 * APPLE] WIRED, how a security researcher discovered the apple battery hack.
- [07/2011 * APPLE] Forbes, Apple laptops vulnerable to hack that kills or corrups batteries.
- [08/2011 * SE] WBUR: Master Hacker Keving Mitnick shares his 'addiction'.
- [06/2011 * PKI] The Register: inside operation "black tulip", Diginotar hack analyzed.
- [03/2011 * PKI] The Register: Comodo hacker brags about forged certificate exploit.
- [12/1010 * DDOS] NU.NL: verdachte van aanval op website OM aangehouden.
- [10/2010 * PHISHING] ZDNET: Crims used hacked email to steal house.
- [11/2010 * PHYSICAL] Gizmodo: how a burnt Lady Gaga CD helped leak thousands of intelligence files.
- [09/2010 * SOCIAL] ZDNET: crims used hacked email to steal house.
- [12/2008 * HASH] The Register: Boffins bust web authentication with game consoles: PS3 fleet spoofs SSL certs.
- [01/2008 * SCADA] The Register: Polish teen derails tram after hacking train network.
- [01/2007 * IOS] PocketLint, this simple text will crash any iPhone, here's how to recover.
- [06/2006 * VOIP] The Register: two charged with VoIP fraud.
- [06/2006 * MALWARE] Trend Micro: Phishing Trojan uses ICMP packets to send data.
- [05/2003 * DDoS] CNET: net attack crushes SCO web site.
- [03/2002 * MALWARE] The Register, law-enforcement DIRT Trojan released.
- [11/2002 * MALWARE] Wired, 'latern' backdoor flap rages.
- [- * -] Wikipedia: AntiSec Movement.
- Learning Culture:
- Leftovers:
- General articles and reads, others:
- Youtube:
##### SECURITY AWARENESS EXAMPLES (EDUCATIONAL) #####
↯
!# HG-0001 - MALWARE DEMO - COMBINED. - Courses: PIA HEXID.
- What: Malware demo with
Trojans, Bots, Rootkits and crypters.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0002 - METASPLOIT & ITUNES & WINAMP. - Courses: PIA HEXID.
- What: Metasploit Winamp attack,
iTunes attack.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0003 - DDOS INTRO WITH SDBOT. - Courses: PIA HEXID.
- What: introduction to DDOS networks
with SDBot, Metasploit, Wireshark, ...
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0004 - INTRODUCTION TO THE MSFCONSOLE. - Courses: PIA HEXID.
- What: introduction to the
Msfconsole, MS RPC, VNC Shell, ...
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0005 - WEP. - Courses: PIA HEXID.
- What: WEP crackingwith
Aircrack-PTW, replay attack.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0006 - NETBOT DDOS. - Courses: PIA HEXID.
- What: DDOS demo with the Netbot
malware, EvilHTTPServer, WireShark and DDoS.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0007 - AANVAL CONSOLE. - Courses: PIA HEXID.
- What: running Snort with
the Openaanval console.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0008 - INTRODUCTION TO IDS WITH SNORT. - Courses: PIA HEXID.
- What: introduction to SNORT
IDS.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0009 - DRIVE BY DOWNLOAD ATTACK. - Courses: PIA HEXID.
- What: script kiddie drive
by download attack with Beast.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0010 - TRIBAL FLOOD NETWORK (TFN). - Courses: PIA HEXID.
- What: first generation bot
network with TFN, Etherape and TCPdump.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0011 - HTTP BASIC AUTHENTICATION. - Courses: PIA HEXID.
- What: HTTP basic
authentication cracking with Brutus.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0012 - FOTKA THE TROJAN SHEEP. !# HG-0013 - APACHE CHUNKED ATTACK ON FREEBSD. - Courses: PIA HEXID.
- What: Apache chunked attack
on FreeBSD.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0014 - BLUESNARFING. - Courses: PIA HEXID.
- What: Bluetooth snarfing on
a Nokia 6310i.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0015 - RPC ATTACK. - Courses: PIA HEXID.
- What: MS RPC service
attack, click kiddie style.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0016 - WIFI WEP CRACKING. - Courses: PIA HEXID.
- What: WEP cracking with Network
Stumbler and Dstumbler, brute force.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0017 - FTP BOUNCE ATTACK. - Courses: PIA HEXID.
- What: execution of a
classic FTP bounce attack.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0018 - SSH PORTFORWARDING. - Courses: PIA HEXID.
- What: demo of SSH
portforwarding.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0019 - ETTERCAP ARP SPOOFING. - Courses: PIA HEXID.
- What: performing a classic
ARP MiTM attack with Ettercap.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0020 - PPTP CRACKING. - Courses: PIA HEXID.
- What: PPTP VPN
authentication cracking.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0021 - OPENVPN. - Courses: PIA LISF.
- What: OpenVPN demo on
Endian FW.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0022 - EXCELL PORTSCAN. - Courses: PIA HEXID
- What: portscanning in
limited environments with MS Excell.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0023 - MS IIS. - Courses: PIA HEXID
- What: Microsoft IIS
exploitation with Extended Unicode. Privilege escalation
with .IDQ and SAM examples.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0024 - SHOUTCAST EXPLOITATION. - Courses: PIA HEXID
- What: Shoutcast
exploitation with hash cracking (John The Ripper) and
rootkit installation.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0025 - REAL VNC AUTHENTICATION BYPASS - Courses: PIA HEXID
- What: Real VNC
Authentication bypass.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0026 - ANI EXPLOIT. - Courses: PIA HEXID
- What: Windows ANI exploit
with Irfanview.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0027 - OPHCRACK. - Courses: PIA HEXID
- What: introduction to OPHCRACK.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0028 - MERCUR MAIL SERVER. - Courses: PIA HEXID
- What: Mercur mail server
exploitation.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0029 - RIP SPOOFING. - Courses: PIA HEXID
- What: routing, RIP
spoofing.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0030 - HONEYPOT WITH HONEYD. !# HG-0031 - AGILENT ANALYZER - VOICE. - Courses: PIA HEXID
- What: VOIP snarfing with
the Agilent Analyzer.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0032 - HTTPRINT. !# HG-0033 - LINUX PTRACE PRIVILEGE ESCALATION. - Courses: PIA HEXID
- What: Linux ptrace local
privilege escalation.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0034 - HASH COLLISION. - Courses: PIA HEXID
- What: demo of MD5 hash
collision.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0035 - CISCO HTTP SERVER. - Courses: PIA HEXID
- What: cracking a Cisco IP
HTTP server, integer overflow.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0036 - MS IIS. - Courses: PIA HEXID
- What: cracking MS IIS with
WebDAV and VNC.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0037 - MS TERMINAL SERVICES - Courses: PIA HEXID
- What: cracking MS Terminal
Services with MS Remote Desktop and "TSGrinder".
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0038 - SNARFING WITH OWNS !# HG-0039 - ENUMERATION VISUAL ROUTE - TRACEROUTE !# HG-0040 - CRACKING MS TERMINAL SERVICES. - Courses: PIA HEXID
- What: cracking MS Terminal Services
with "tscrack" and AI.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0041 - IKE FINGERPRINTING. !# HG-0042 - STERM !# HG-0043 - SERVU - SEH attack.. - Courses: PIA HEXID
- What: executing an attack against
SERVU.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0044 - MS TERMINAL SERVICES. - Courses: PIA HEXID
- What: executing a brute
forcing attack on MS terminal services.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0045 - SMB DICTIONARY ATTACK, SNMP - Courses: PIA HEXID
- What: executing a SNMP dictionary
attack.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0046 - SMB DICTIONARY ATTACK. - Courses: PIA HEXID
- What: executing a SMB dictionary
attack.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0047 - CDP SPOOFING. - Courses: PIA HEXID
- What: spoofing Cisco CDP
messages.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0049 - CDP DOS. - Courses: PIA HEXID
- What: denial of service
through CDP messages.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0049 - DICTIONARY ATTACK. - Courses: PIA HEXID
- What: word list generation
and dictionary attack.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0050 - URL SPOOFING. - Courses: PIA HEXID
- What: classic URL spoofing
with Mozilla Firefox.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0051 - BASIC MAIL SPOOFING. - Courses: PIA HEXID
- What: classic and basic
mail spoofing.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0052 - METASPLOIT. - Courses: PIA HEXID
- What: Metasploit with a
VNCShell and MS DCOM exploit.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0053 - SCRIPTKIDDIE DOS. - Courses: PIA HEXID
- What: DoS concept, script
kiddie style (SMB2/Negotiate DoS).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0054 - DEBIAN OPENSSH ATTACK (PRNG). - Courses: PIA HEXID
- What: Debian PRNG OpenSSH attack.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0055 - EVIL MAID. - Courses: PIA HEXID
- What: Evil Maid attack demonstration
on Truecrypt.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0056 - PRIVILEGE ESCALATION (WINDOWS 7). - Courses: PIA HEXID
- What: privilege esclation
concept on Windows 7 (RING/CVE-2010-0232).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0057 - FUZZING. - Courses: PIA HEXID
- What: fuzzing demonstration with
TAOF and WarFTP
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0058 - RAINBOW TABLES. - Courses: PIA HEXID
- What: rainbow table demonstration on
the MS Windows platform.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0059 - ZEUS/ZDBOT. - Courses: PIA HEXID
- What: malware demonstration
with ZEUS/ZDBOT, Metasploit (MS_IE_2010).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0060 - PRIVILEGE ESCALATION ON UBUNTU. - Courses: PIA HEXID
- What: privilege escalation concept
on Ubuntu 10.X LTS using
PAM MOTD local privilege escalation vulnerability.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0061 - BOTNET CREATION WITH IFRAMES. - Courses: PIA HEXID
- What: malware distribution
(SDBOT) by deploying iframes and Metasploit.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0062 - NEXPOSE. - Courses: PIA HEXID
- What: introduction to
Nexpose of Rapid7.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0063 - NESSUS v4. - Courses: PIA HEXID
- What: introduction to
Nessus v4.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0064 - SCRIPT KIDDIE DDOS. - Courses: PIA HEXID
- What: introduction to
script kiddie style DoS feat. Ion Cannon (4Chan).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0065 - CHECK POINT R71 IPS. - Courses: PIA Security
- What: introduction to Check
Point IPS (R71), short demo.
Featuring Traffic IQ Pro.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0066 - CHECK POINT R71 IPS. - Courses: PIA Security
- What: introduction to Check
Point IPS (R71), long demo.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0067 - BOTNET DETECTION WITH NIKSUN. - Courses: PIA HEXID
- What: introduction to
botnet detection with Niksun,
Arcsight, Tufin, full packet capture.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0068 - INTRODUCTION TO STACK BASED BUFFER OVERFLOWS. - Courses: PIA HEXID
- What: introduction to stack
based buffer overflows (x86).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0069 - SESSION HIJACKING.. - Courses: PIA HEXID
- What: introduction to
session hijacking with Firesheep (WiFi).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0070 - SMBDIE. - Courses: PIA HEXID
- What: introduction to the
DoS attacks, CIFS SMBDIE.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0071 - SLOWLORIS ATTACK. - Courses: PIA HEXID
- What: introduction to
the Slowloris/Pyloris, DoS attack.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
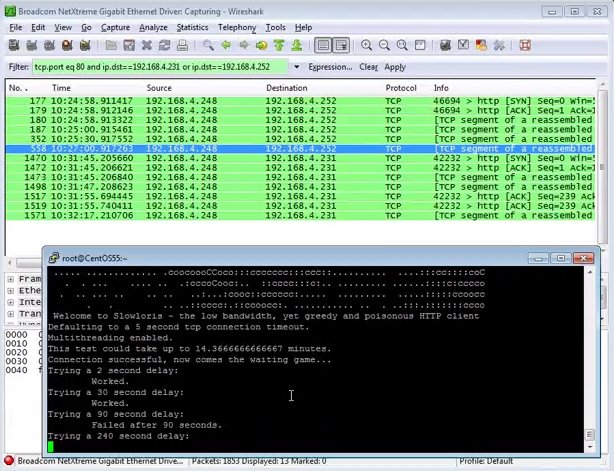
!# HG-0072 - PRIVILEGE ESCALATION (PIPEUPADMIN) - Courses: PIA HEXID
- What: introduction to
privilege escalation concept(PipeUpAdmin).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0073 - ESSENTIAL KERBEROS CRACKING. - Courses: PIA HEXID
- What: introduction to
cracking, Kerberos.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0074 - ESSENTIAL RIP SPOOFING. - Courses: PIA HEXID
- What: introduction to
spoofing, RIP.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0075 - DISTRIBUTED & CUDA CRACKING. - Courses: PIA HEXID
- What: introduction to
distributed cracking, CUDA, Elcomsoft, OpenOffice.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0076 - CORE IMPACT - Courses: PIA HEXID
- What: introduction to CORE
IMPACT; explaining Rapid Penetration Test (RPT).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0077 - CORE IMPACT (CLIENT SIDE). - Courses: PIA HEXID
- What: introduction to CORE
IMPACT; client side phishing campaign.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0078 - SECURE EMAIL (S/MIME). - Courses: PIA Security
- What: secure email demo
with S/MIME and MS AD CS (PKI, OSCP, CRL, ...).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0079 - VASCO DIGIPASS. - Courses: PIA Security
- What: authentication with VASCO
Digipass solutions (IDENTIKEY).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0080 - IPV6 RA DOS (CVE-2010-4669). - Courses: PIA HEXID.
- What: causing DoS using
IPv6 RA's.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0081 - CISCO MDS 9000 - FIBER CHANNEL INTRO - Courses: PIA Storage Fundamentals.
- What: introduction to Fibre
Channel (FC) on Cisco MDS FC switches.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0082 - TREND MICRO DEEP SECURITY 9. - Courses: PIA Data Center Security.
- What: introduction and
malware demo with Trend Micro Deep Security 9
on VMware ESXi.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0083 - CHECK POINT GAiA R76, HA CLUSTER. - Courses: PIA Data Center Security.
- What: essential Check Point
GAiA HA cluster.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0084 - CHECK POINT VE ON VMWARE ESXi. - Courses: PIA Data Center Security.
- What: essential Check Point
Virtual Edition (VE).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0085 - MICROSOFT HYPER-V 2012R2 - Courses: PIA Data Center Security.
- What: essential Microsoft
Hyper-V 2012 R2 clustering and live migration.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0086 - INTRODUCTION TO VSPHERE 5.5. - Courses: PIA Data Center Security.
- What: essential VMware
vSphere concepts.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0087 - IPSEC CONFIGURATION ON CHECK POINT GAiA. - Courses: PIA Data Center Security.
- What: essential IPSEC concepts on
Check Point GAiA (Hide NAT).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0088 - HIDE NAT CONFIGURATION ON CHECK POINT GAiA. - Courses: PIA Data Center Security.
- What: basic NAT concept on
Check Point GAiA (Hide NAT).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0089 - FIREWIRE ATTACK. - Courses: PIA HEXID.
- What: exploiting firewire to get
access to remote memory (bus).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0090 - ANDROID INFORMATION LEAK - Courses: PIA HEXID.
- What: exploiting an Android
information leak using Metasploit, Android
Development Toolkit, browser.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0091 - NTLMv1 attack. 
!# HG-0092 - SMB RELAY. - Courses: PIA HEXID.
- What: creating a basic Android
reverse shell.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
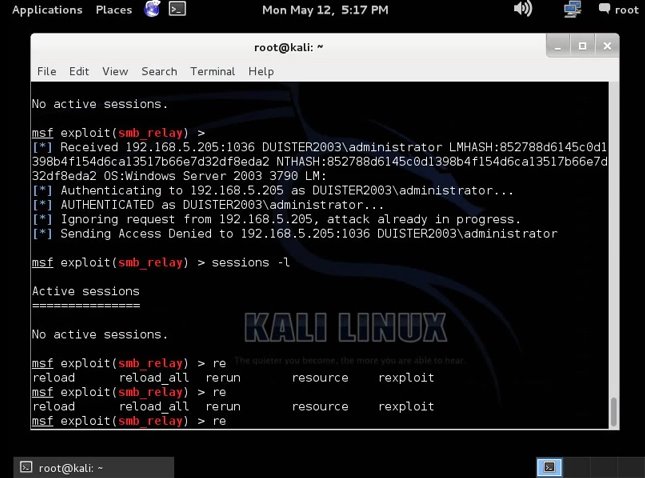
!# HG-0093 - ANDROID REVERSE SHELL - Courses: PIA HEXID.
- What: creating a basic Android
reverse shell.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0094 - ANDROID RAT - Courses: PIA HEXID.
- What: introduction Android
malware, Android RAT.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0095 - ANDROID LOCKSCREEN PROTECTION - Courses: PIA HEXID.
- What: bypassing an Android
physical lock screen.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0096 - ANDROID ASM ROOTING - Courses: PIA HEXID.
- What: introduction Android
Rooting with ASM.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0097 - SSH CRACKING WITH CRUNCH. - Courses: PIA HEXID.
- What: introductionto Crunch
and deploying word lists against
SSH users.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0098 - SMTP SPOOF. 
!# HG-0099 - SIP. - Courses: PIA HEXID.
- What: introduction to SIP
enumeration and account cracking.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0100 - SIP CRACKING. - Courses: PIA HEXID.
- What: introduction to SIP
challenge-response cracking (MD5).
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0101 - NESSUS INTRODUCTION ON KALI LINUX. - Courses: PIA HEXID.
- What: introduction to Nessus on Kali Linux
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0102 - OPENVAS DEPLOYMENT ON KALI LINUX. - Courses: PIA HEXID.
- What: introduction to OpenVAS.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0103 - SQL ENUMERATION AND METASPLOITABLE INTRODUCTION. - Courses: PIA HEXID.
- What: introduction to Metasploitable
and basic SQLi.
- Play with
HTML5.
Play with Flash.
Play on Youtube.

!# HG-0104 - MALICIOUS PDF - Courses: PIA HEXID.
- What: demonstration of a
malicious pdf.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0105 - METASPLOIT KEYSCAN - Courses: PIA HEXID.
- What: demonstration of the
Metasploit keyscan feature.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0106 - JAVA AUTOPWN - Courses: PIA HEXID.
- What: demonstration of the
Metasploit Autopwn feature with Java.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0106 - JAVA AUTOPWN - Courses: PIA HEXID.
- What: demonstration of the
Metasploit Autopwn feature with Java.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0107 - NFS + JOHN THE RIPPER - Courses: PIA HEXID.
- What: demonstration of NFS
abuse with John the Ripper
and Metasploitable.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0108 - SQLi (DVWA). - Courses: PIA HEXID.
- What: demonstration of SQLi
with DVWA.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0109 - METASPLOIT CRASH COURSE - Courses: PIA HEXID.
- What: demonstration of the
Metasploit framework
with a quick overview.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0110 - METASPLOIT + MSFVENOM - Courses: PIA HEXID.
- What: demonstration of the
Metasploit framework
with MSFVENOM.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0111 - SSL MITM + ETTERCAP - Courses: PIA HEXID.
- What: demonstration of the
Ettercap NG framework with
a SSL MiTM attack.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0112 - SSLSTRIP MITM. - Courses: PIA HEXID.
- What: demonstration of the
SSLSTRIP framework
to perform a MiTM.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0113 - VEIL FRAMEWORK. - Courses: PIA HEXID.
- What: demonstration of the
Veil Framework and
basic AV evasion.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0114 - SOCIAL ENGINEERING TOOLKIT (SET). - Courses: PIA HEXID.
- What: demonstration of the
Social Engineering Toolkit (SET)
with ARP & DNS spoofing.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0115 - EVILGRADE. - Courses: PIA HEXID.
- What: demonstration of the
EvilGrade MiTM attack.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0116 - DRUPAL 7 SQLi - Courses: PIA HEXID.
- What: demonstration of the
script kiddie
SQL Injection exploitation of Drupal 7.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0117 - SHELLSHOCK RECON - Courses: PIA HEXID.
- What: demonstration of the
shellshock vulnerability
by abusing a web server using the Burp suite.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0118 - MAC OS X SUDO PRIVILEGE ESCALATION - Courses: PIA HEXID.
- What: demonstration of
privilege escalation concept
on Mac OS X using the "sudo" vulnerability.
- Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0119 - MAC OS X ROOTPIPE - Courses: PIA HEXID.
- What: demonstration of
privilege escalation concept
on Mac OS X using the "rootpipe" vulnerability.
Infection through malicious Java payload. - Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0120 - UAC PRIVILEGE ESCLATION - Courses: PIA HEXID.
- What: demonstration of
privilege escalation concept
on Windows 7 using an UAC vulnerability. - Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0121 - TIMESHIFTER - Courses: PIA HEXID.
- What: demonstration of time-based,
cover network channels
using POC "Timeshifter". - Play with
HTML5.
Play with Flash.
Play on Youtube.
!# HG-0122 - WIFITE - Courses: PIA HEXID WIFI.
- What: demonstration of automated
wifi attacks using the PoC "Wifite".
Play with HTML5.
Play with Flash.
Play on Youtube.
!# HG-0123 - ROGUE, SOFT-AP WITH AIRBASE-NG AND ALFA AWUS036H. - Courses: PIA HEXID WIFI.
- What: creating a rogue, software AP
for a single SSID by using
Airbase-NG and an ALFA wNIC on Kali Linux 2.
Play with HTML5.
Play with Flash.
Play on Youtube.
!# HG-0124 - ROGUE, SOFT-AP WITH HOSTAPD AND ALFA AWUS036NHA. - Courses: PIA HEXID WIFI.
- What: creating a rogue, software AP
for a single SSID by using
Hostapd, Kali 2.x 32bit on a physical machine.
Play with HTML5.
Play with Flash.
Play on Youtube.
!# HG-0125 - CAPTURING PROBE REQUESTS WITH THE ALFA AWUS036NHA. - Courses: PIA HEXID WIFI.
- What: capturing WiFi probe requests
with Kali 2.x 32bit on a physical machine.
Play with HTML5.
Play with Flash.
Play on Youtube.
!# HG-0126 - AIRBASE-NG KARMA MODE WITH THE ALFA AWUS036NHA. - Courses: PIA HEXID WIFI.
- What: airbase-ng, with Karma Mode, Kali 2.x 32bit on a physical machine.
Play with HTML5.
Play with Flash.
Play on Youtube.
!# HG-0127 - WEP CRACKING WITH AIRCRACK-NG. - Courses: PIA HEXID WIFI.
- What: aircrack-ng, Kali 2.x 32bit on
a physical machine and the ALFA wNIC
with atheros chipset. Executing the DEAUTH and ARP-replay attack.
Play with HTML5.
Play with Flash.
Play on Youtube.
!# HG-0128 - WPA2/PSK CRACKING WITH AIRCRACK-NG. - Courses: PIA HEXID WIFI.
- What: aircrack-ng, Kali 2.x 32bit on
a physical machine and the ALFA wNIC
with atheros chipset. Executing a WPA2/PSK attack.
Play with HTML5.
Play with Flash.
Play on Youtube.
!# HG-0129 - SHELLSHOCK - THE MISSING PRIVILEGE UPGRADE. - Courses: PIA HEXID.
- What: the missing privilege upgrade
after the Shell Shock attack ;).
Play with HTML5.
Play with Flash.
Play on Youtube.
!# HG-0130 - BLANCCO: DISK WIPING. - Courses: PIA HEXID/PIA DC SEC.
- What: secure disk wiping with
BLANCCO.
Play with HTML5.
Play with Flash.
Play on Youtube.
!# HG-0131 - KARMA WITH PINEAPPLE Mk V - Courses: PIA HEXID.
- What: Karma attack and co with the
Pineapple Mk V.
Play with HTML5.
Play with Flash.
Play on Youtube.
!# HG-0132 - GOPHISH - Courses: PIA HEXID.
- What: security awareness campaign
with phishing, using a test run
of GoPhish.
Play with HTML5.
Play with Flash.
Play on Youtube.
!# HG-0133 HEXID T.R.E.N.C.H. - DIRTYCOW/POKEMON - Courses: PIA HEXID.
- What: DIRTYCOW Linux exploitation
of PoCs.
Play with HTML5/FLASH (auto-detect).
!# HG-0134 HEXID T.R.E.N.C.H. - LSASS DoS (MS16-137) - Courses: PIA HEXID.
- What: PoC by Laurent GAffie on MS16-137.
Play with HTML5/FLASH (auto-detect).
!# HG-0135 HEXID T.R.E.N.C.H. - MS SMB Tree Connect DoS - Courses: PIA HEXID.
- What: PoC by Laurent GAffie on CVE 2017-0016.
Play with HTML5/FLASH (auto-detect).
!# HG-0136 HEXID T.R.E.N.C.H. - GENERIC RANSOMWARE DEMO. - Courses: PIA HEXID.
- What: MOD of Hidden Tear, educational ransomware.
Play with HTML5/FLASH (auto-detect).
!# HG-0137 HEXID T.R.E.N.C.H. - MACRO + PRIV. ESCALATION + PERSISTANT BACKDOOR. - Courses: PIA HEXID.
- What: classic macro and Metasploit deployments.
Play with HTML5/FLASH (auto-detect).
!# HG-0138 HEXID T.R.E.N.C.H. - HPING3 ICMP TUNNEL. - Courses: PIA HEXID.
- What: ICMP tunnel with HPing3.
Play with HTML5/FLASH (auto-detect).
!# HG-0139 HEXID T.R.E.N.C.H. - IODINE DNS TUNNEL. - Courses: PIA HEXID.
- What: DNS domain tunnel with Iodine.
Play with HTML5/FLASH (auto-detect).
!# HG-0140 HEXID T.R.E.N.C.H. - ON THE FLY BACKDOORS AND CODE CAVES. - Courses: PIA HEXID.
- What: on the fly backdoor with MITMf and more.
Play with HTML5/FLASH (auto-detect).
!# HG-0141 HEXID T.R.E.N.C.H. - RESPONDER. - Courses: PIA HEXID.
- What: WPAD and LLMNR spoofing with NTMLv2 craking.
Play with HTML5/FLASH (auto-detect).
!# HG-0142 HEXID T.R.E.N.C.H. - RESPONDER AND WPAD SPOOFING. - Courses: PIA HEXID.
- What: WPAD spoofing - MiTM Proxy.
Play with HTML5/FLASH (auto-detect).
!# HG-0143 HEXID T.R.E.N.C.H. - VSFTPD BACKDOOR. - Courses: PIA HEXID.
- What: vsftpd backdoor on Metasploitable 2.
Play with HTML5/FLASH (auto-detect).
!# HG-0144 HEXID T.R.E.N.C.H. - ETERNALBLUE AND PUTTY SSH HIJACKING. - Courses: PIA HEXID.
- What: Metasploit ETERNALBLUE and incognito and PuttyRider.
Play with HTML5/FLASH (auto-detect).
!# HG-0145 HEXID T.R.E.N.C.H. - SMBLoris DOS AGAINST A WINDOWS 10 PHYSICAL HOST. - Courses: PIA HEXID.
- What: SMBLoris against a Windows 10 host.
Play with HTML5/FLASH (auto-detect).

!# HG-0146 HEXID T.R.E.N.C.H. - SMBLORIS DoS AGAINST VMS ON ESXI 6.x. - Courses: PIA HEXID.
- What: SMBLoris against a Windows 10 and 7 VMs on ESXi 6.x.
Play with HTML5/FLASH (auto-detect).

!# HG-0147 HEXID T.R.E.N.C.H. - BeEF ESSENTIALS (Man In The Browser (MITB)). - Courses: PIA HEXID.
- What: BeEF .js hooking, SE and Metasploit payload execution
Play with HTML5/FLASH (auto-detect).

!# HG-0148 HEXID T.R.E.N.C.H. - SSH MiTM PROXY. - Courses: PIA HEXID.
- What: SSH MiTM, proxy usage
Play with HTML5/FLASH (auto-detect).

!# HG-0148B HEXID T.R.E.N.C.H. - PKI PRIMER WITH TLS (MS 2012R2 AD & IIS). - Courses: PIA Cyber Security Explored / PKI Primer.
- What: introduction to PKI and TLS on a MS 2012R2 infrastructure
Play with HTML5/FLASH (auto-detect).
!# HG-0149 HEXID T.R.E.N.C.H.- HASH COLLISIONS (MD5 AND SHA-1). - Courses: PIA HEXID.
- What: different example hash collisions (MD5/SHA-1).
Play with HTML5/FLASH (auto-detect).
!# HG-0150 HEXID T.R.E.N.C.H - SQLi basics. - Courses: PIA HEXID.
- What: SQL injection basics in the HEXID TRENCH cyber range.
Play with HTML5/FLASH (auto-detect).
!# HG-0151 HEXID T.R.E.N.C.H - forensic image creation: STUXNET. - Courses: PIA HEXID.
- What: creating a forensic target with a STUXNET related vulnerability.
Play with HTML5/FLASH (auto-detect).
!# HG-0152 HEXID T.R.E.N.C.H - introduction to Volatility (memory forensics). - Courses: PIA HEXID.
- What: analysing a basic memory image.
Play with HTML5/FLASH (auto-detect).
!# HG-0153 HEXID T.R.E.N.C.H - classic lateral movement. - Courses: PIA HEXID.
- What: drive-by-download, priv. escalation, pass-the-hash, Metasploit Pivot.
Play with HTML5/FLASH (auto-detect).
!# HG-0154 - TraceWrangler. - Courses: PIA HEXID.
- What: sanitization and anonymization of PCAP(ng) files.
Play with Not publicly available, sorry..
!# HG-0155 - NTMLv1 SMB C/R and John The Ripper. - Courses: PIA HEXID.
- What: updated video on NTML v1 CR.
Play with Not publicly available, sorry..
!# HG-0156 - traffic flows with Ntop and IDS with Security Onion. - Courses: PIA HEXID.
- What: demo of Ntop and Security Onion
Play with Not publicly available, sorry..
!# HG-0157 - PTP-RAT, data exfiltration using colour codes (RDP) - Courses: PIA HEXID.
- What: deployment of PTP-RAT (PenTestPartners.com) to demonstrate data ex-filtration with color codes (steganography)
Play with HTML5/FLASH (auto-detect).
!# HG-0159 - Bettercap, SSL/TLS, HSTS - Courses: PIA HEXID.
- What: deployment of PTP-RAT (PenTestPartners.com) to demonstrate data ex-filtration with color codes (steganography)
Play with HTML5/FLASH (auto-detect).
!# HG-0160 - Red Hat Enterprise Linux, DHCP client exploitation - Courses: PIA HEXID.
- What: RHEL Linux DHCP client exploitation with dnsmasq
Play with HTML5/FLASH (auto-detect).
!# HG-0201 - Memcached, Python and Scapy - Courses: PIA HEXID.
- What: Memcached PoC with Scapy and Python
Play with HTML5/FLASH (auto-detect).
!# HG-0202 - Social Engineering, Bash Bunny, USB & Responder - Courses: PIA HEXID.
- What: Security awareness with HAK5 Bash Bunny, Responder and USB
Play with HTML5/FLASH (auto-detect).
!# HG-0203 - Social Engineering, Rubber Ducky HID & USB - Courses: PIA HEXID.
- What: Security awareness with HAK5 Rubber Ducky, USB and HID
Play with HTML5/FLASH (auto-detect).
!# HG-0204 - PoC test of Vi CVE-2019-12735 - Courses: PIA HEXID.
- What: Security awareness with trusty files and Vi(m).
Play with HTML5/FLASH (auto-detect).
!# HG-0205 - Core Impact Intro Demo (2019) - Courses: PCU HEXID.
- What: introduction to the Core Impact Framework (2019).
Play with HTML5/FLASH (auto-detect).
All rights reserved - PIA, PCU, PXS, giechelbit.duister.org, 2001-2019.
Crazy Mouse Logo is a licensed logo of the related cyber security courses.
All examples were executed on private lab systems.
Information provided can only be used as educational and awareness examples.
Original authors and developers are mentioned where available.
Opinions, products, conclusions, ... referenced are not endorced.
